Hi everyone, today we’re going to do the Capture! room on TryHackMe.
This room is about a company that developed a Web Application, and, to prevent hackers from bruteforcing their login page, implemented a rate limiter it.
The first task makes us download a zip file, which contains a relatively long list of usernames and passwords. We are most probably going to need to bypass the rate limitation to try them all and find the right combination.
Once the machine finishes booting up, we can take a look at the login page :

If we try to test a username and password combination, we get this error message :
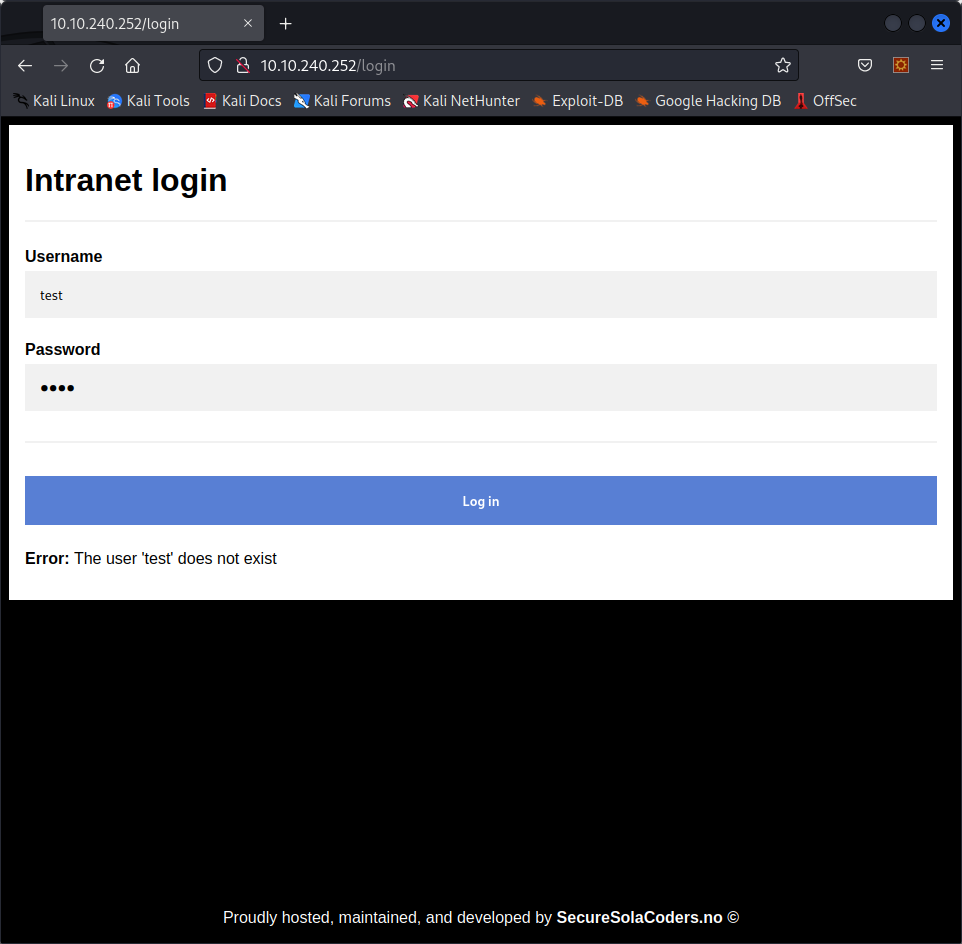
Hmm, it looks like the username and password are checked separately, and we get different error messages if the username is unknown and if the password is wrong. That is great for us, we just went from a keyspace in O(n2) to one in O(n).
Let’s use Hydra with the usernames we got from the zip file.
First, we check the request that is sent when we try to login :
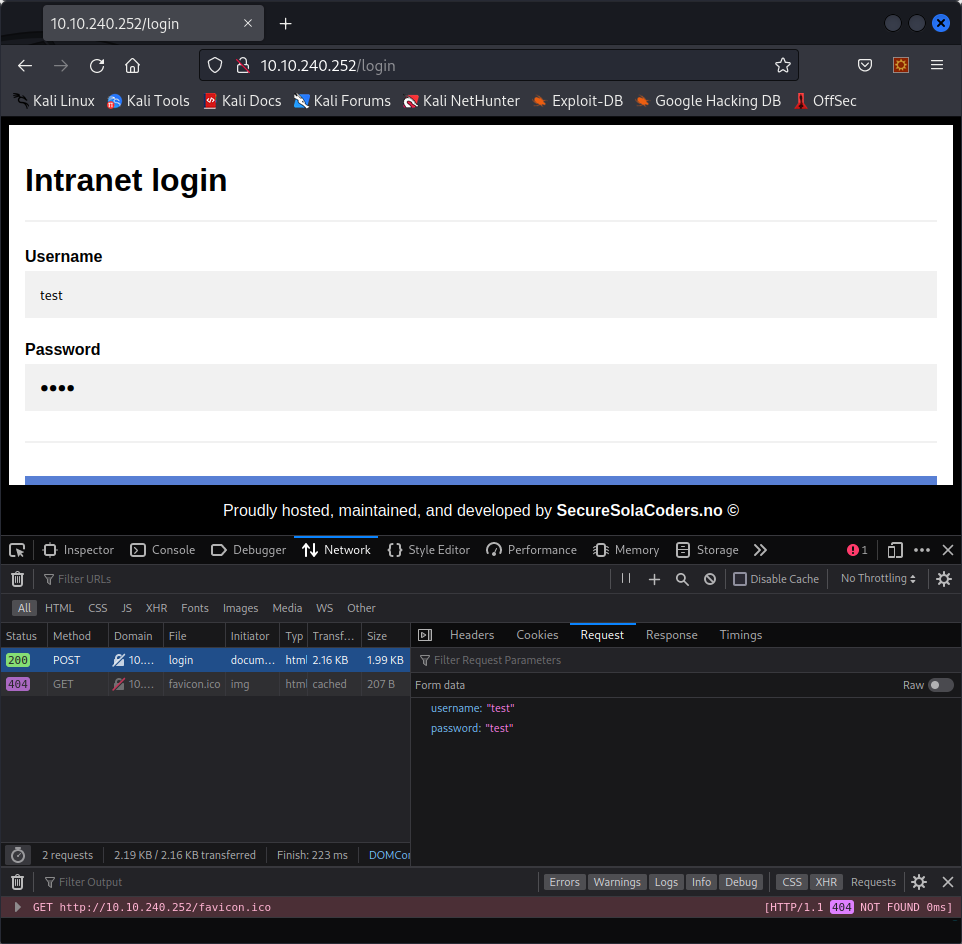
It is a POST request with two parameters : username and password.
So, our command will be :
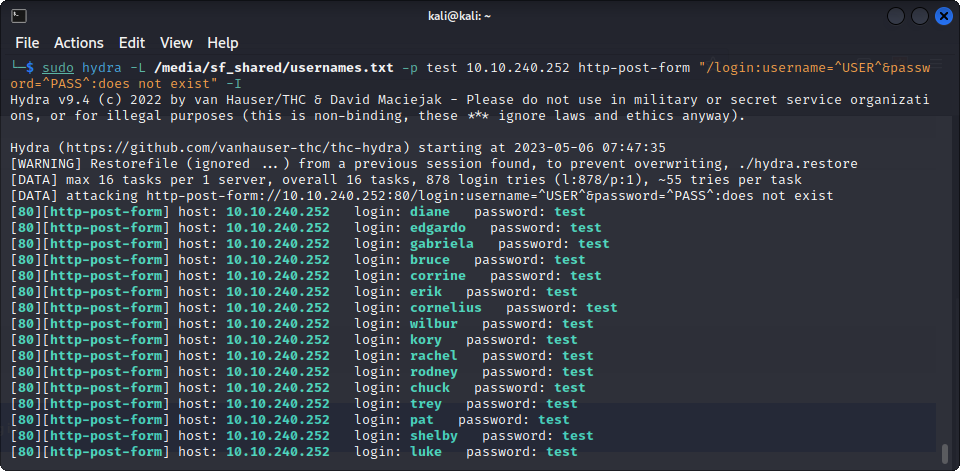
sudo hydra -L $USERNAMES_LIST -p test $TARGET_IP http-post-form "/login:username=^USER^&password=^PASS^:does not exist" -IBut, when launching it, we see many successful requests, which is obviously not correct :
If we reload the page, this is what we see :
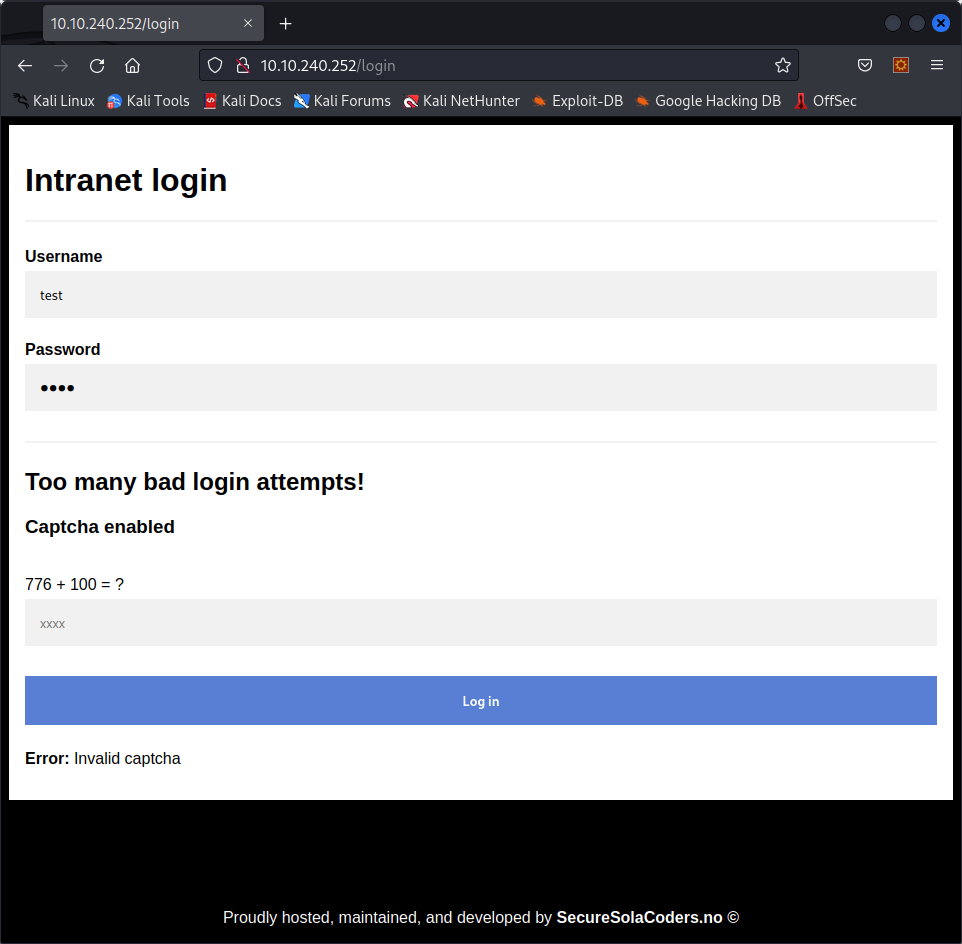
So this is the rate limiter they implemented! After a few attempts, we need to solve a simple equation to send more requests. Fortunately for us, the captcha looks simple enough to be solved by a machine.
To do just that, we are going to create a small python script that uses the requests module to get the webpage, parse it to get and solve the captcha, and the send it back with a login attempt.
I have uploaded my script on GitHub. While the script is not well-written, it does the job.
It works by making 10 requests, to be sure to get to the rate limiter. Then, it searches the responses for the captcha using a regex, and solves it using the exec function. While using the exec function is really unsafe (it could lead to arbitrary code execution on the machine running the script), I won’t bother much for this. After that, it tries another username, and prints it if the response didn’t contain the string “does not exist”.
Running it, we get a match for a username :

Good, now we can move on to trying to find the corresponding password. This is the error we get when trying a random password for this user :
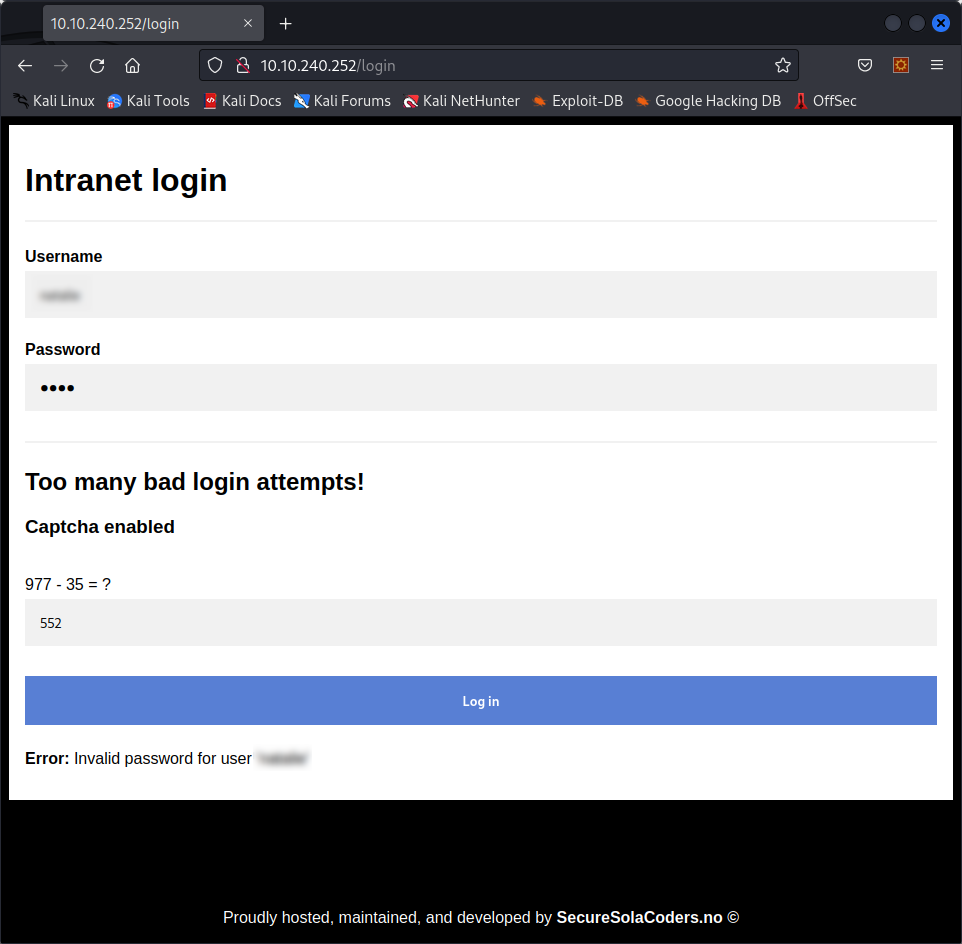
Now, we can slightly modify the script from earlier to get the password. I have uploaded it to the same repository as before.
Here is the result :

Yay, now, we can login in the app, and find our flag :

Hurray! We completed this room !
I hope you enjoyed this, and found this room entertaining. I certainly did. With that said, see you later !

Leave a Reply