Hi ! Today we are going to take a look at the MD2PDF machine on TryHackMe ! This machine is a web server hosting a service that allows us to convert markdown files to PDFs. If not done properly, it is easy to miss something when developing this kind of applications and have a big hole in it. This is what we are going to try to find here.
The first thing we are going to do is take a look at the application. Here, it is pretty simple, with a textbox to input our markdown, and a button to convert it to a PDF.
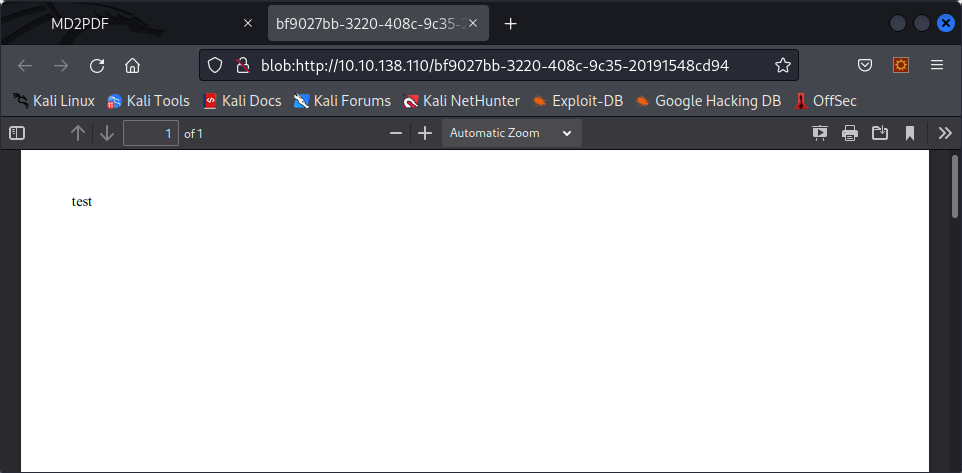
When inputting a simple test, it opens a new window with the generated PDF :
The website seems to be working as expected. The next step will be to scan it with nmap, to see what services are running on the machine.
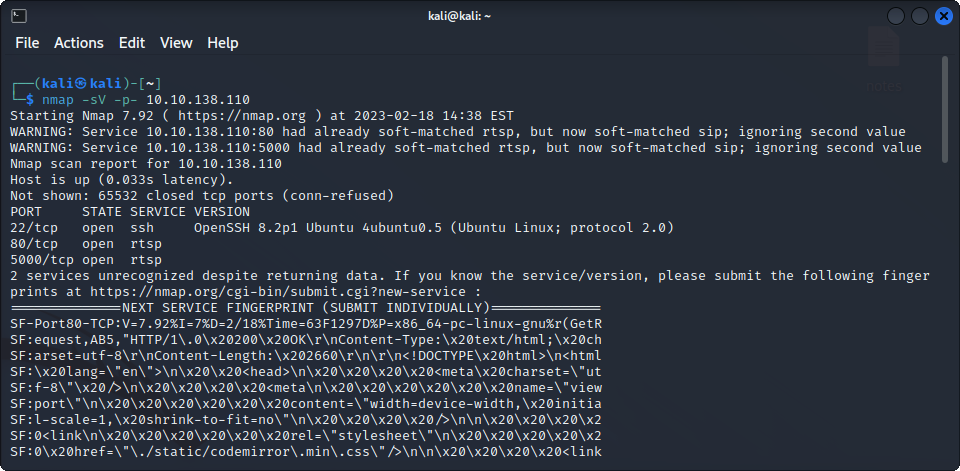
We find an ssh server, and two unrecognized services running on ports 80 and 5000. We already know that port 80 is holding the webpage, and, after visiting it, it seems that port 5000 is serving the same page as port 80.
When trying to enumerate directories, we find two pages : /admin and /convert. /convert is the endpoint a POST request with the markdown data is sent to when converting a file, and /admin looks to be inaccessible from the outside.
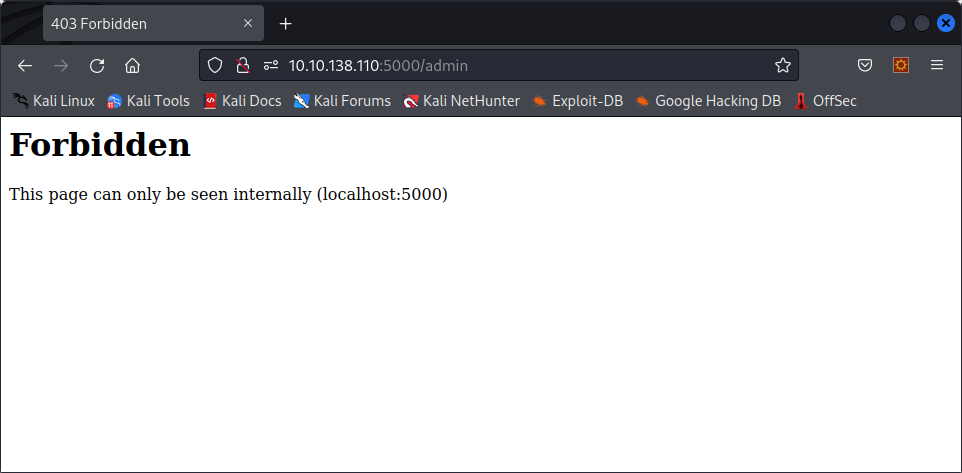
When we did the Stocker machine, we injected iframes into a pdf to get access to a local file. Maybe we can use something similar here to access the admin page.
Well, indeed inputting this into the markdown input :
<iframe src='http://localhost:5000/admin' width='1000' height='1000'>Gives us a PDF showing the admin page, which contains the flag we were looking for :
Yay ! This machine was a nice quick refresher on iframe injection. I hope you enjoyed it as much as I did !

Leave a Reply