Hi, this time, I am creating the challenge instead of solving it !
Here it is :
UEsDBBQAAQAAANuISVZAP3X6MAAAACQAAAANAAAAcHJpbnRfZmxhZy5zaGEKNwnnVLkZfh0Y5/dAWQeI3jtPHAWDGvAIwtT9CaWCom/cmEsTzQiN7S6ceX9qLFBLAQI/ABQAAQAAANuISVZAP3X6MAAAACQAAAANACQAAAAAAAAAgAAAAAAAAABwcmludF9mbGFnLnNoCgAgAAAAAAABABgAACPphqA82QHcMQ6YoDzZAWhbEpCgPNkBUEsFBgAAAAABAAEAXwAAAFsAAAAAAA==Good luck, hints and a writeup are below in case you need any help.
Hints
Solution
As we can see by the two equal signs at the end of the challenge, it is base64 encoded data. When we try to decode this data, we get this :
PK����ۈIV@?u0���$���
���print_flag.sha
7 T~@Y;O oܘK.yj,PK?�����ۈIV@?u0���$���
�$��������������print_flag.sh
� ��������#醠<1<h[<PK������_���[�����Doesn’t look too appealing, does it ? The “print_flag.sh” bit is interesting, but it doesn’t give much. In fact, the most interesting bytes here are the two bytes at the beginning : PK. These are the magic bytes one can find on ZIP files. This means that this data is likely to be a zip file.
We can turn this base64 string into a zip file using the command :
echo "base64string" | base64 --decode > challenge.zipThis will decode the data and save it to a file called “challenge.zip”. We can now take a look at this file using 7zip :
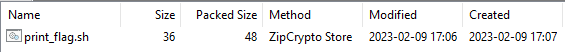
This zip file holds a single file called print_flag.sh, probably the one we need to complete this challenge. Unfortunately for us, it is password protected. We can try to bruteforce the password, but it won’t work in this case because the password is too strong. We need to find another method to extract this file.
If we look at the method used to store the file, we can see that it is using ZipCrypto, and not AES, this means that it should be vulnerable to Biham and Kocher’s known plaintext attack ! This means that if we know at least 12 bytes of the file (with at least 8 contiguous ones), we can crack open this archive !
We just need to find some part of the file. One thing we could look at are the magic bytes, but in this case, a bash script is just a text file, so it doesn’t have any special markers. They have one particularity though, they sometimes begin with a shebang indicating the shell used to execute the script, so it it reasonable to assume that the script begins with :
#!/bin/bashThis is plenty of known plaintext for our purpose ! This means that we can now start the attack. One thing that could cause some problems is the characters at the end of the line, on Windows, it would be \r\n, but on Linux, which is probably what was used to create this file, it would only be \n. Since the two are quite similar, this can sometimes lead to false positives where the file appears cracked but cannot be deciphered. To be sure, we can either ignore them, or try both versions if one does not work.
Using Bkcrack, we can now crack the archive, and create a new one with the same contents and a password that we know :
bkcrack -C challenge.zip -c print_flag.sh -p plain.txtto recover the keys, and :
bkcrack -C challenge.zip -k key1 key2 key3 -U cracked.zip password123to create a new file called cracked.zip, with the password “password123”
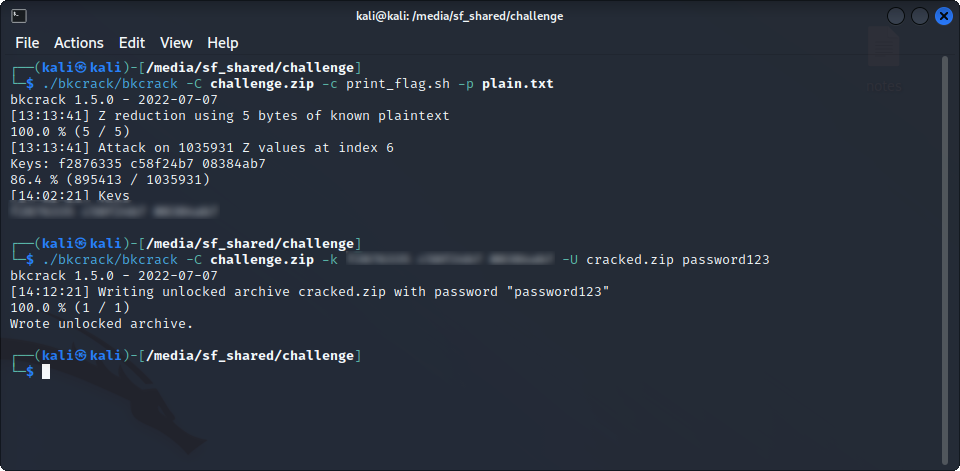
It worked ! We can now extract the file, and execute it to get out flag :
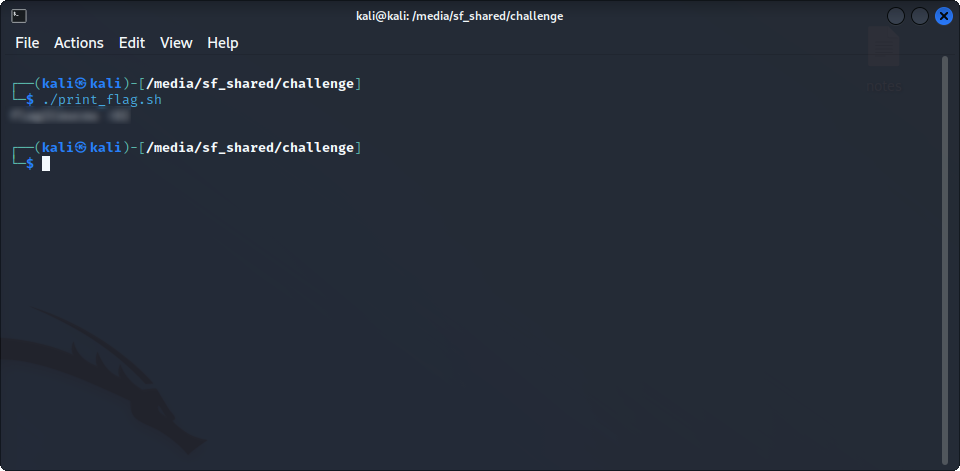
Yay ! I hope you enjoyed this little challenge and maybe learned a useful thing or two while trying to solve it !
hide the solution
Leave a Reply