Hi ! Today we’re going to take a look at the TakeOver room on TryHackMe. As its description states, this challenge revolves around subdomain enumeration.
As advised by the author, the first thing to do is add the provided IP for futurevera.thm to our /etc/hosts file in order to resolve the URL on our machine.
Once, that is done, we can take a first look at the website :
This looks like a basic company website, nothing special in the cookies or in the source of the page, so we move on.
The next step I took was to scan the ports of the target machine :
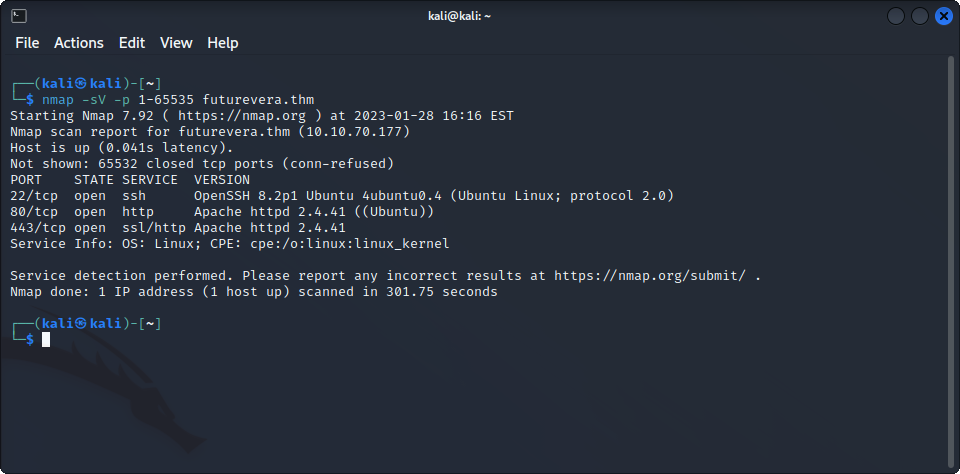
As expected, we can see an Apache server on ports 80 and 443. However, there doesn’t seem to be any DNS service running on the machine. Since .thm is not a real tld (top-level domain), there also won’t be any information on public DNS servers. This means that in order to find subdomains of this website, we are probably going to need to use virtual hosts enumeration.
To do this, we’re going to use ffuf, with the command
ffuf -w $wordlist -H "Host: FUZZ.futurevera.thm" -u https://futurevera.thm -acin order so send requests to the website, but with different subdomains in the Host header to see if any of them return anything special. We’re going to run this command on both HTTP and HTTPS protocols, to see if anything comes up. I used this wordlist. Here are the results :
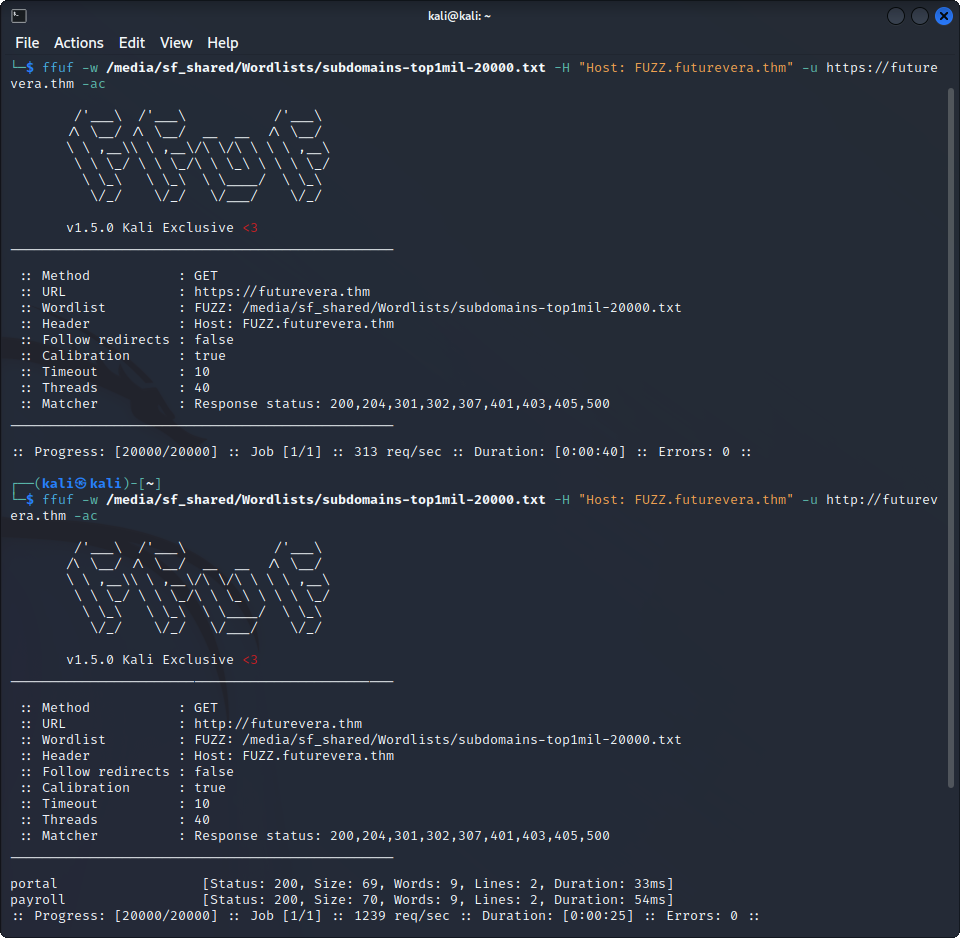
Yay ! We found two subdomains ! Let’s add them to /etc/hosts and see whats on them :
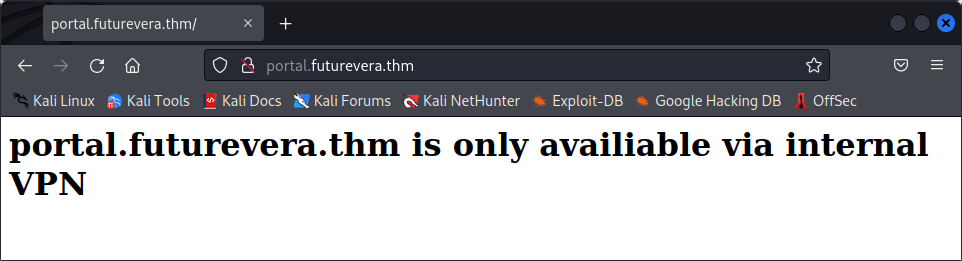
Well, unfortunately, nothing interesting is on these two pages. We have to dig deeper, but where ? The wordlist I tried contains 20.000 guesses, and this is an easy challenge, so it is likely in there. Isn’t it a bit weird that we found HTTP subdomains but no HTTPS subdomain ? Maybe there was a problem with the way we ran ffuf ? Let’s try it without the -ac flag and without rejecting any response code using the -mc all flag to see what kind of responses we are getting :
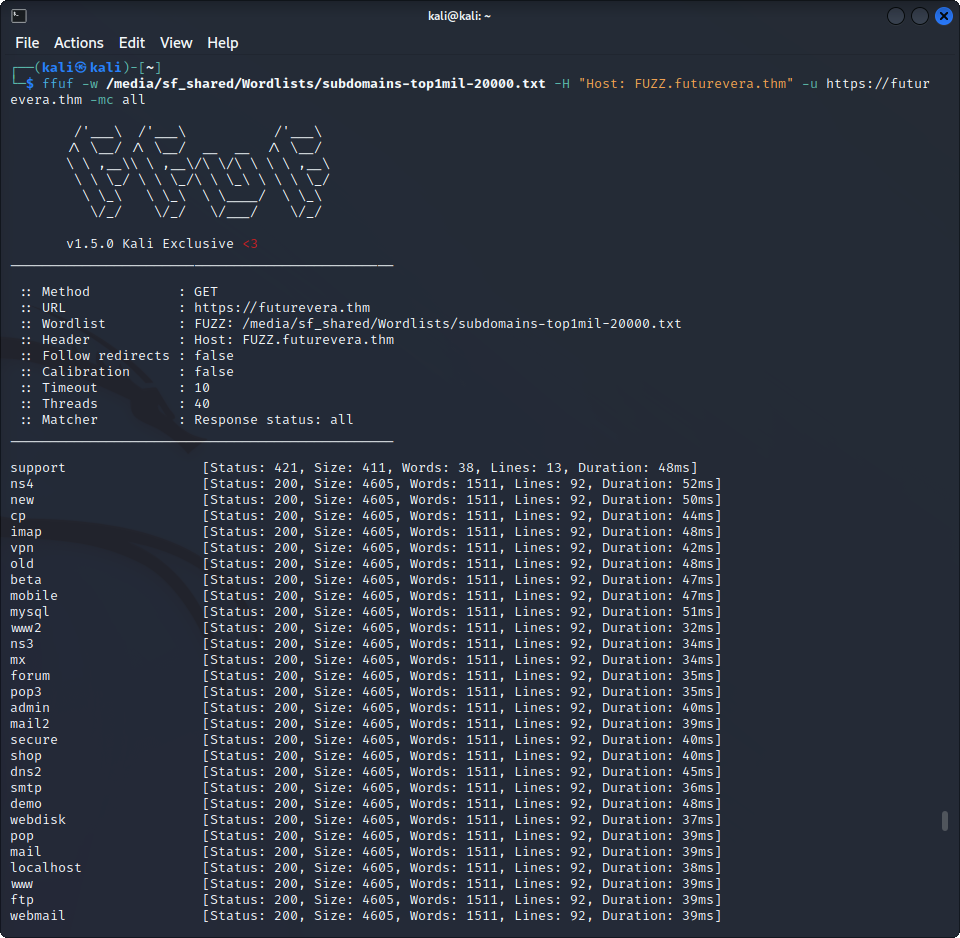
Suddenly, everything matches ! That’s not going to help us, is it ? But wait, the first try resulted in a different response code than all of the others here : 421 misdirected request. Could it be that https://support.futurevera.thm is a valid subdomain ? Let’s first re-run ffuf while filtering the answers that are 4605 bytes long :
ffuf -w $wordlist -H "Host: FUZZ.futurevera.thm" -u https://futurevera.thm -mc all -fs 4605Bingo, we find three more subdomains :
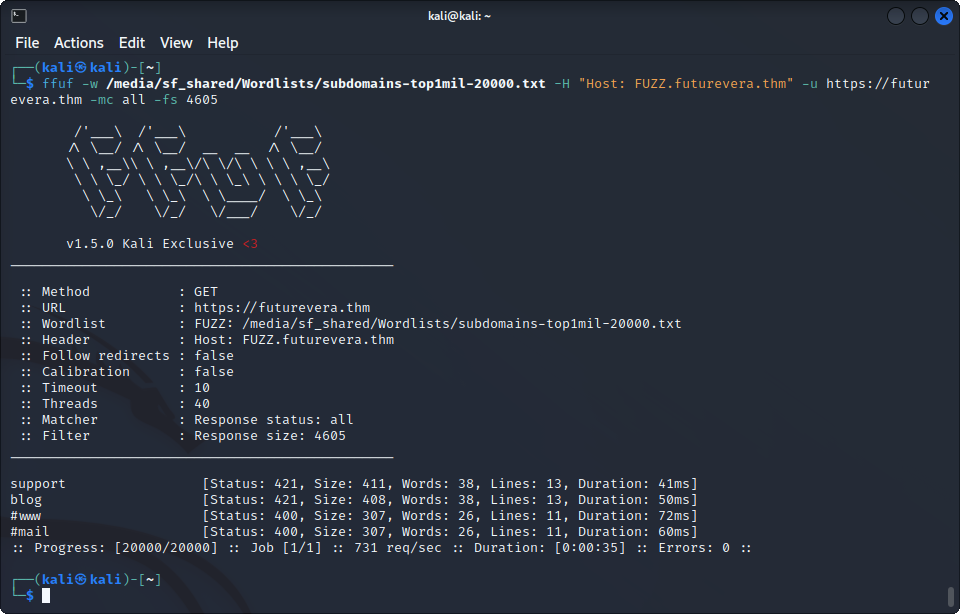
#www and #mail are probably errors judging from the 400 code they returned, so we’ll ignore them, at least for now. Let’s add the two other subdomains to /etc/hosts and visit them :
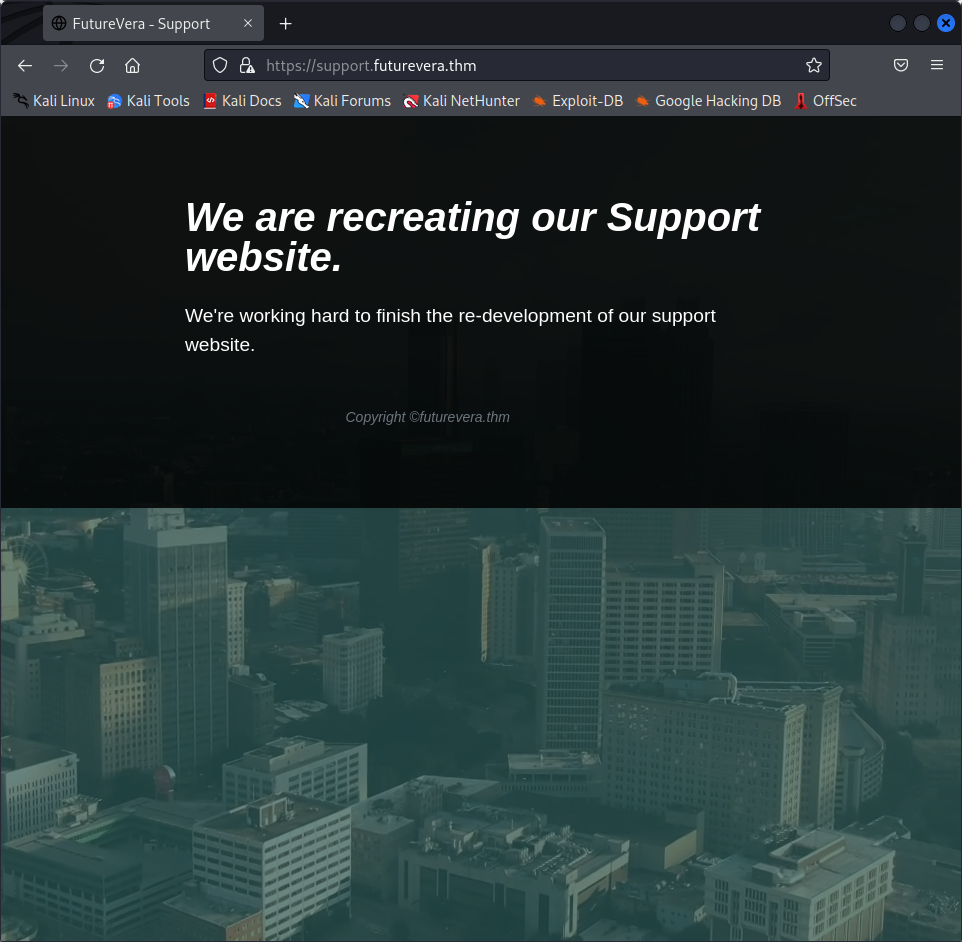
They look more promising than the two HTTP subdomains we found before. However, searching the source code and trying to enumerate directories did not return anything useful. Are we in a dead end again ? What is different between http and https ?! : https uses certificates to prove the identity of the server, and these certificates usually contain useful information about the domain !
Look at what we find in the certificate for https://support.futurevera.thm :
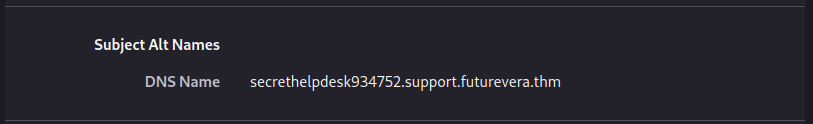
Let’s also make this domain point to the IP of the target machine and visit it. The flag suddenly appears in front of our eyes :
We can now enter it and get the points !
I hope you found this interesting and helpful !

Leave a Reply